Recent interviews for the state of email security are in for 2022, and we are seeing more of the same that has been reported in years past. In an interview surrounding Email Security Best Practices, VP of Barracuda, Mike Flouton, discusses the different kinds of email attacks, and the best email security practices to follow to protect your emails and sensitive data.
The 2022 Q&A responses show the following results:
- Phishing is one of the most common types of email threats seen today, whether that be URL or spear-phishing
- Business email compromise (BEC), also referred to as CEO fraud or wire-transfer fraud, is a less common, but costly type of spear-phishing attempt
- Even though BEC makes up only 9% of all spear-phishing attacks, it caused more than $2.4B in losses in 2021 alone
- About 32% of breaches involving some type of phishing, and may include malicious links to fraudulent websites (URL)
- However, only 57% of organizations have URL protection in place and 74% of organizations have fallen victim to a phishing attack
- 91% of cyberattacks begin with an email, and there are 13 email threat types
- Therefore, email protection should be a #1 priority for organizations
Here are 5 steps that organizations can take immediately to reduce risks posed by email cybercriminals in 2023:
1. Upgrade email security from Office 365
Microsoft’s Office 365 email security, known as Advanced Threat Protection, is about 3 years behind technology already in the market from other security vendors. Review of your current email and malware protection systems are an essential element of proper security planning.
Email security products, built by Barracuda Networks, Proof point and Mimecast, all provide advanced protection for email, which provide defense against spam and malware delivery.
These systems have superior technical capabilities to Microsoft Advanced Threat Protection (ATP), such as an integrated ability to whitelist or mark domains as safe, and scanning for embedded malware threats.
Barracuda Email Protection
Barracuda Email Protection is a comprehensive, easy to use solution for organizations that are seeking protection for their businesses, brands, and people. This service delivers gateway defense, API-based inbox defense, incident response, data protection, and compliance capabilities.
Barracuda uses advanced techniques to detect known spam and malware. It also provides email continuity, along with outbound filtering and encryption, to prevent data loss. Built-in Advanced Threat Protection uses payload analysis and sandboxing to discover zero-day malware.
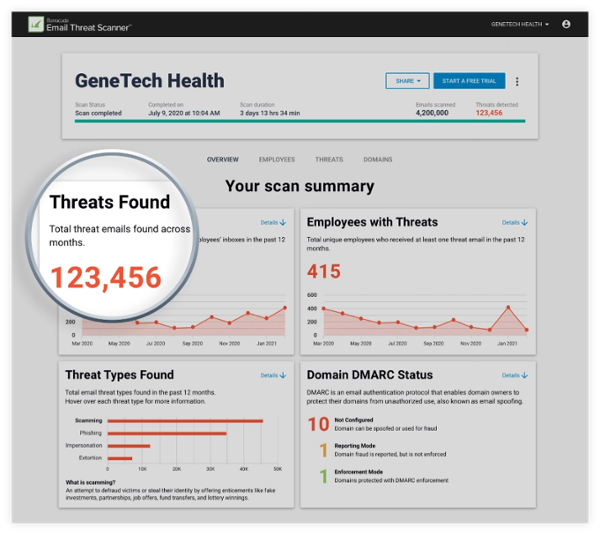
Barracuda Email Threat Scan
98% of organizations without Microsoft 365 have malicious emails in their mailboxes. Barracuda Email Threat Scanner has identified more than 100 million spear phishing attacks sitting in organizations' email environments.
Utilizing artificial intelligence and API integration with Microsoft 365, Barracuda Email Threat Scanner identifies which of your employees are the most targeted by attackers. This will directly show you which of your employees is most vulnerable to a breach.
2. Audit Current Security Infrastructure
To understand and identify the deficiencies that likely exist in security infrastructure and to prioritize spending to fix the issues, leaders should conduct frequent audits of their security infrastructure.
This includes but is not limited to their training programs, existing security solutions, and the processes implemented to remediate security incidents.
A Formal Security Compliance Document is Essential
You will need an information security plan, which will include:
- System configurations
- Data retention and deconstruction policies
- Policies for outsourced software development
- Acceptable use policies
- Encryption policies
- Implementation requirements
- Password requirements
This document should provide the framework for how employees handle, share and store sensitive data.
The policy should address password management systems and password policies. It should also look at how frequently data is backed up and acceptable use policies for employee and company owned devices, applications, and services.

3. Build a Multi-Layer Defense for Email Security
Additional layers beyond basic email security that protect against the ever increasing sophistication of attacks, include sandboxing attachments, time of click URL analysis, and A/I scanning of email and attachments.
We also suggest that firewall perimeter security and network access control systems are reviewed for security effectiveness, as part of a comprehensive security plan.
Sandboxing
Sandboxing is a technique in which you create an isolated test environment to execute a suspicious file or URL. If this file or URL is attached to an email or otherwise reaches your network, it is critical to observe that activity closely. If the file or URL displays malicious behavior, then you've discovered a new threat.
Advanced Threat Protection
Barracuda's Advanced Threat Protection is a sophisticated cloud service that delivers the benefits of sandboxing while eliminating the drawbacks of more traditional, stand-alone sandboxing solutions.
Unlike more traditional virtual-machine sandboxing, Barracuda's Advanced Threat Protection uses a CPU-emulation sandbox. From the malware's perspective, it will remain indistinguishable from a real desktop machine.
A/I Scanning
A/I email scanning is critical for your organization to take part in, as it reviews every email message for potential viruses, malware, and spam. It also evaluates links/attachments for signs of email spoofing, which are generally used in an impersonation attack.
Many email scanning services, like Mimecast and Barracuda, can scan all inbound, outbound, and internal emails, equipping your team with all the necessary protection against threats.
Outbound email scanning is important, considering malicious actors can have an internal presence within your organization, or employees might not be aware when they send infected emails.

4. Review Your Office 365 Tenant Security Settings
We have personally witnessed attacks on O365 tenants that have taken advantage of clients. This is due to the lack of priority in reviewing or modifying default security settings within their email cloud service. Review your O365 security rules that govern basic security for the service.
The fewer administrators making changes in your organization, the better! Make sure that all IT personnel authorized to make changes use a domain admin password, instead of their personal credentials.
Also, be sure to prevent any rule change originating from a source address outside of your domain, (this is a common way for criminals to initiate account takeovers).
Tenant Allow/Block List
Using the Microsoft 365 Defender Portal, you can create block entries for domains and email addresses directly in the Tenant Allow/Block List.
Email messages from these senders are marked as high confidence spam (SCL = 9). What happens to the messages is determined by the anti-spam policy that detected the message for the recipient.
In the default anti-spam policy and new custom policies, messages that are marked as high confidence spam are delivered to the Junk Email folder by default. In Standard and Strict preset security policies, high confidence spam messages are quarantined.
Users in the organization won't have access to send emails to these blocked domains and addresses. Instead, they will receive a non-delivery report, also known as a bounce message that will state:
"5.7.1 Your message can't be delivered because one or more recipients are blocked by your organization's tenant allow/block list policy." This will ensure that employees don't send sensitive data to any potential scammers.
5. Implement E-Mail Usage Best Practice and Regular Cloud Backup Procedures
All employees, in particular Sr. Executives, and Financial/Accounting Dept. Employees, should be aware of the risks of providing personal information on social media accounts that can be used by cybercriminals.
All employees should adopt passwords on email systems, which are very different from personal accounts in use.
Further, all email systems, including Office 365 email, should be regularly backed up by an outside cloud service, as Microsoft does not guarantee data beyond 30 days within Office 365.
Barracuda Email Protection Plan
With a Barracuda Email Protection Plan, you can get cloud backup for Office 365 data, including Exchange Online mailboxes, SharePoint online, OneDrive for Business, and Teams.
This plan provides fast point-in-time recovery in the event of accidental or malicious deletion. Cloud archiving helps you meet compliance requirements with e-discovery, granular retention policies, and unlimited storage.
Only Barracuda protects against all 13 email threat types, from spam and ransomware to socially engineered threats, like spear-phishing, account takeover, and business email compromise.

Conclusion
See what threats are hiding in your Microsoft 365 inboxes. Sign Up Now for a free Microsoft 365 Email Threat Scan with no impact to your email performance.




