In today's dynamic cybersecurity landscape, it is imperative for organizations to implement resilient solutions that enable swift and efficient detection and response to malicious activities. Azure Sentinel, Microsoft's cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) solution, stands at the forefront of modern threat detection and hunting capabilities.
Azure Sentinel empowers organizations to proactively defend against sophisticated cyber threats, providing a comprehensive platform for security operations and incident response. In this blog, we will be taking a look at how Azure Sentinel can detect cyber threat intelligence in your environment, identify patterns and indicators of compromise, and much more!
What is Azure Sentinel?
Azure Sentinel serves as a centralized platform, aggregating and analyzing vast amounts of security data from various sources like applications, devices, servers, and user activities. Leveraging the power of artificial intelligence and machine learning, it identifies potential security incidents and provides valuable insights for proactive threat hunting. With its flexibility, scalability, and seamless integration with Microsoft's security ecosystem, Azure Sentinel empowers security professionals with the essential arsenal to outsmart cyber threats and safeguard valuable assets and data with utmost efficiency.
Introduction to Threat Intelligence
Cyber Threat Intelligence (CTI) includes information about existing or potential threats to systems and users. It can take various forms, from written reports on threat actors' motivations, techniques, and infrastructure to specific observations of IP addresses, domains, file hashes, and other artifacts linked to known cyber threats.
CTI helps organizations understand unusual activities and respond quickly to protect their people, information, and assets. It is sourced from diverse places, including open-source data feeds, threat intelligence sharing communities, commercial intelligence feeds, and local intelligence gathered during security investigations.
For SIEM solutions like Azure Sentinel, the most common form on CTI is threat indicators, also known as Indicators of Compromise (IoC) or Indicators of Attack (IoA). These threat indicators link observed artifacts like URLs with known threat activities such as phishing, botnets, or malware.
Tactical threat intelligence refers to this type of intelligence, as it is applied to security products and automation on a large scale to detect potential threats and protect organizations. By using threat indicators in Azure Sentinel, you can detect malicious activity in your environment and provide essential context to security investigators, aiding their response decisions.
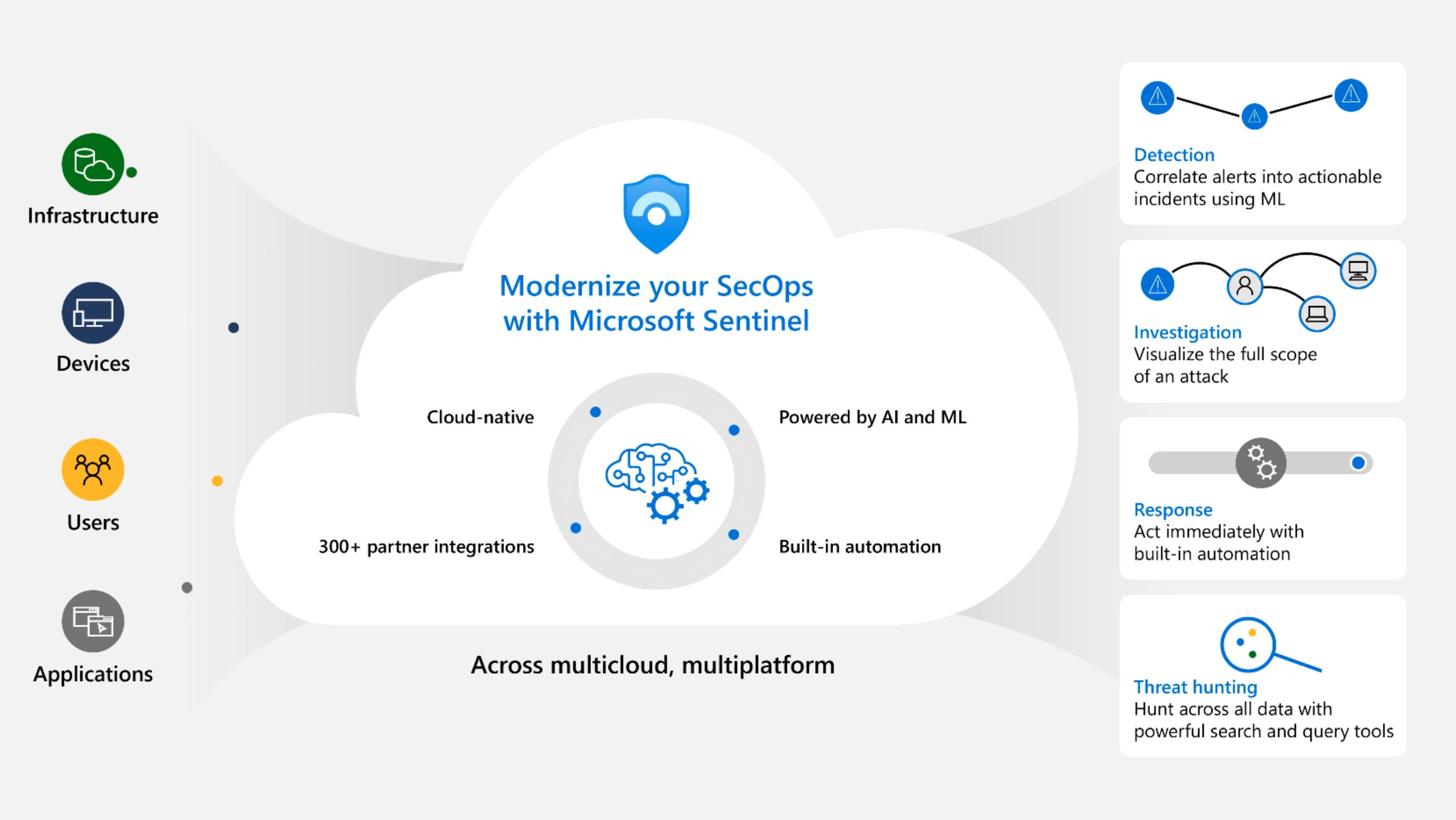
How to Integrate with Azure Sentinel
Threat intelligence (TI) can be integrated into Sentinel through the following activities:
- Incorporate threat intelligence into Azure Sentinel by activating data connectors that link to various TI platforms and feeds.
- Access and manage the integrated threat intelligence in Logs and the Threat Intelligence blade of Azure Sentinel.
- Identify potential threats and generate security alerts and incidents using the pre-built Analytics rule templates that rely on your imported threat intelligence.
- Visualize essential details about your integrated threat intelligence in Azure Sentinel with the Threat Intelligence workbook.
Import threat intelligence with data connectors
Just like all the other event data in Microsoft Sentinel, threat indicators are imported using data connectors. Here are the data connectors in Microsoft Sentinel provided specifically for threat indicators:
- Microsoft Defender Threat Intelligence data connector to ingest Microsoft's threat indicators
- Threat Intelligence - TAXII for industry-standard STIX/TAXII feeds
- Threat Intelligence upload indicators API for integrated and curated TI feeds using a REST API to connect
- Threat Intelligence Platform data connector also connects TI feeds using a REST API, but is on the path for deprecation
You have the flexibility to utilize any combination of these data connectors, depending on where your organization obtains threat indicators. All three of these connectors can be found in the Content Hub as part of the Threat Intelligence solution. For more information about this solution, see the Azure Marketplace entry Threat Intelligence.
Also, see this catalog of threat intelligence integrations available with Microsoft Sentinel.
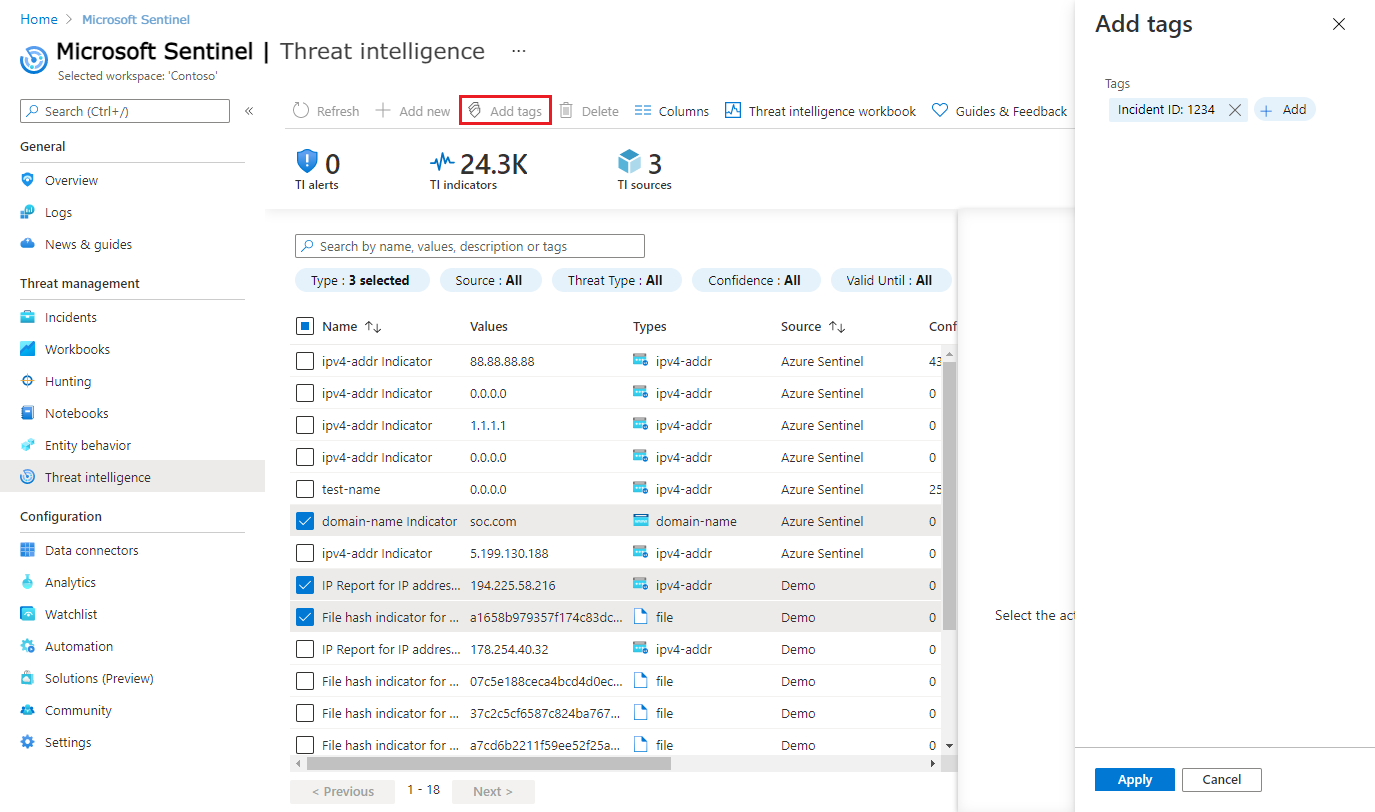
Centralized Visibility and Data Aggregation
At the core of Azure Sentinel's capabilities is its ability to collect and aggregate security data from various sources. Organizations can integrate data from on-premises resources, cloud services, applications, devices, and third-party solutions into a centralized workspace. This unified data repository provides security analysts with a comprehensive view of their entire IT environment. With all security data in one place, Azure Sentinel enables real-time monitoring and analysis, allowing teams to quickly identify anomalous activities and potential security threats.
AI-Powered Analytics for Threat Detection
Azure Sentinel leverages the power of artificial intelligence and machine learning to detect emerging threats and anomalous behavior. The platform employs built-in machine learning algorithms and models to analyze vast amounts of security data rapidly. By continuously learning from historical data, Azure Sentinel can identify patterns and indicators of compromise (IOCs) that human analysts might miss. These AI-driven analytics not only improve detection accuracy but also reduce the time it takes to identify and respond to security incidents, helping organizations stay one step ahead of cyber attackers.
![]()
Proactive Threat Hunting
Azure Sentinel enables proactive threat hunting, allowing security analysts to actively search for indicators of compromise and potential threats. Using custom queries and filters, analysts can explore security data and conduct in-depth investigations to uncover hidden or emerging threats. This proactive approach is essential for identifying and mitigating threats that may not trigger traditional alerting mechanisms. Azure Sentinel's threat hunting capabilities empower security teams to take a proactive stance in identifying and neutralizing threats before they escalate into full-blown incidents.
Automated Incident Response
Incident response is a critical aspect of effective threat detection. Azure Sentinel streamlines incident response through automated playbooks and workflows. Security teams can create custom playbooks that define response actions based on specific scenarios. These playbooks automate repetitive and time-consuming tasks, enabling faster containment and remediation of security incidents. Furthermore, integrating Azure Sentinel with other security and SOAR tools enhances overall response capabilities, making incident handling more efficient and reducing the workload on security teams.
Customization and Flexibility
All organizations have unique security requirements Azure Sentinel offers customization options to tailor the platform to specific needs. Security analysts can create custom dashboards, workbooks, and alerts to focus on the most critical security events and metrics. The flexibility of Azure Sentinel allows organizations to adapt the platform as their security needs evolve over time.
Workbooks provide insights to your threat intelligence
Workbooks offer an immersive experience with interactive dashboards that provide valuable insights into every aspect of Microsoft Sentinel. This includes threat intelligence, which plays a crucial role in keeping organizations secure. By utilizing the powerful Threat Intelligence workbook, you can easily visualize key information about threats and customize it to align with your business needs.
You can even create new dashboards that combine various data sources, allowing you to visualize your data in unique and meaningful ways. With these workbooks, you can take advantage of extensive documentation and a wide range of templates, making it easier than ever to explore and analyze your threat intelligence.

Final Thoughts
Azure Sentinel serves as a powerful tool for organizations seeking to enhance their threat detection and hunting capabilities. By leveraging the cloud's scalability, artificial intelligence, and machine learning, Azure Sentinel empowers security teams to detect and respond to security incidents rapidly and effectively.
With centralized data collection, AI-driven analytics, threat intelligence integration, proactive threat hunting, and automated incident response, Azure Sentinel offers a comprehensive solution to safeguard critical assets and data against sophisticated cyber threats. Embracing Azure Sentinel as part of a robust cybersecurity strategy equips organizations with the agility and resilience needed to stay ahead of adversaries in today's dynamic threat landscape.
Contact us today to find out how Azure Sentinel can detect cyber threat intelligence in your environment and to gain insight on how to seamlessly integrate this solution into your Microsoft ecosystem.




