In today's digital-driven business landscape, where conducting online transactions is prevalent, the significance of NIST in the realm of cybersecurity cannot be overstated. Security is increasingly crucial for organizations operating in the digital world, and NIST plays a pivotal role in ensuring their protection.
Despite the exponential growth of data, numerous companies still neglect the implementation of adequate cybersecurity measures. By disregarding the importance of complying with general standards and security regulations, these companies unknowingly expose themselves to potential problems in the long term.
However, when companies align themselves with NIST's comprehensive set of guidelines, they gain a distinct advantage over their counterparts lacking NIST knowledge. Not only does this alignment enable them to circumvent the issues faced by non-compliant organizations, but it also equips them with a structured framework that operates in accordance with globally recognized standards. This adherence to NIST standards fosters a culture of robust security and ensures that businesses are better prepared to safeguard their digital assets and sensitive information.
| TABLE OF CONTENTS |
What is NIST?
NIST (National Institute of Standards and Technology) is responsible for establishing technology, standards, and metrics to be applied to the scientific and tech industries.
NIST was founded in 1901, in the United States, as a division of the Department of Commerce (DOC). NIST’s campus was originally located at the intersection of Connecticut Ave. and Van Ness in Washington, D.C.
As one of the oldest science labs in the country, it plays a crucial role in the operation of businesses in both the private and public sectors. The main purpose of NIST (and the reason for its creation) is to promote competition and innovation within an industry.
NIST compliance supports the smallest to the biggest and most complex of devices and hardware. This ranges from nanoscale devices to global communication networks. NIST focuses specifically on data security and cybersecurity.
What does NIST do?
NIST provides a set of guidelines on how to adequately protect data. With this framework, a company can accurately assess what security measures must be followed to guarantee that its data remains safe. NIST outlines this set of standards that provide a high degree of uniformity in the cybersecurity realm, which is critical to the success of any business.
NIST's guidelines and standards are widely recognized and adopted globally, making it a crucial resource for businesses operating in the digital world. Compliance with NIST standards not only ensures enhanced cybersecurity but also helps organizations establish trust with their customers, partners, and stakeholders. By adhering to NIST's recommendations, companies can effectively address the evolving cyber threats and mitigate risks in today's interconnected and technology-driven business environment.
What is NIST Compliance?
Compliance is the act of adhering to the NIST guidelines. By doing this, organizations keep up their compliance standards even with the twists and turns of an evolving tech environment. This includes making changes as the business' vulnerabilities shift and as the cybersecurity landscape transforms.
Maintaining compliance is crucial to your company because it not only protects the data, but also the people whose lives are affected by the data.
Benefits
NIST Compliance benefits your business of operations for the following reasons:
- Protects against malware, ransomware, and other cyber threats
- Helps avoid extreme costs associated with security risks (a successful hack)
- Mitigates the impact of lost or compromised data
- Secures sensitive information
- Maintains trustworthy reputation with your customers
- Helps to avoid ensuing legal trouble that comes after a cybersecurity breach
Who is it important to and why?
All business that is conducted with the United States government must comply with NIST. This includes agencies within the U.S. government, as well as businesses and individuals that the government may hire to perform work on projects.
In addition, those who might conduct government business in the future should comply as well. This removes a potential hurdle during the bidding process.
At times, NIST compliance may even be included in the contract you sign with a government agency. It is important to carefully read all contracts to see if NIST compliance is a requirement.
Along with this, a subcontractor who is hired by a company to perform work for the government should also make sure they are NIST-compliant. By doing this, they are in alignment with the company’s efforts to secure jobs.
The following are individuals who will be required to adhere to NIST guidelines:
- Defense contractors
- Educational and/or research institutions that handle federal data
- Financial and health services organizations
- Telecommunication service providers
If you would like more information on solutions for meeting compliance requirements within your organization, check out Our Ultimate Guide to the Microsoft Compliance Manager.

How Can NIST help protect your data?
NIST standards are formed on the most up to date practices in the tech environment. The government suggests companies use them regularly. Among NIST’s guidelines, the most widely used is the NIST Cybersecurity Framework (CSF).
NIST New Adaptation: CSF
First launched in 2014, NIST Cybersecurity Framework (CSF) is a set of guidelines designed to assist in establishing cybersecurity strategies.
CSF identifies cybersecurity risks first. Upon identification, it details methods to reduce the severity of the risks. According to an article recently published on Balbix, "The NIST cybersecurity framework is a powerful tool to organize and improve your cybersecurity program. It is a set of guidelines and best practices to help organizations build and improve their cybersecurity posture. The framework puts forth a set of recommendations and standards that enable organizations to be better prepared in identifying and detecting cyber-attacks, and also provides guidelines on how to respond, prevent, and recover from cyber incidents."
According to the US Chamber of Commerce, "Among the sectoral associates are auto manufacturers, the chemical industry, gas industry, hotels, water works, communications, electrical distribution, financial services," and many others.
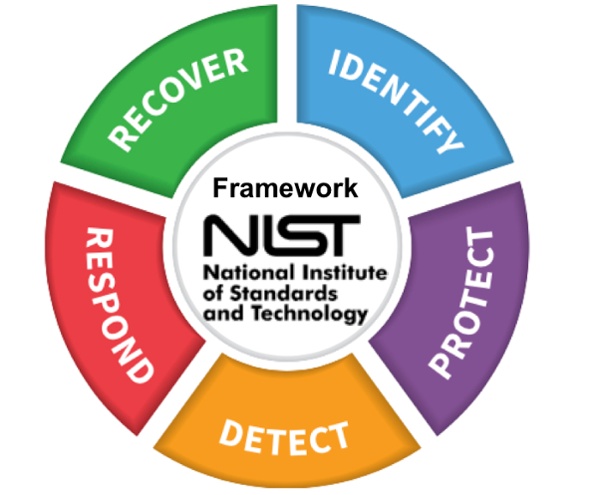
The Framework
The NIST Cybersecurity Framework outlines all the ways in which data needs to be protected to create a more secure organization. To ensure protection from malicious actors and code, this outline is followed.
It is composed of five steps:
- Identify: Systems that need to be protected are identified in this step. This involves those that fall under the jurisdiction of specific legislation, designed to protect consumers, patients, and sensitive information.
- Protect: The team puts security measures in place to safeguard the data. This includes tools, software, and hardware with the intention of addressing security concerns. It also adds in onboarding stakeholders and employees, allowing everyone to work as a unit in guarding sensitive data and systems.
- Detect: In the detection phase, tools and policies are designed to discover an incident once it occurs. This calls for enhanced visibility into systems, devices, and networks that are utilized by the organization. It also includes applications that manage data during regular business.
- Respond: In this phase, a company creates a plan of action for responding to a threat. Your company must determine which tools and methods will be used to mitigate the threat. An organization’s response mechanism may include some systems built to approach a threat from different angles (antivirus software or redundant firewalls).
- Recover: This process is characterized by ways of helping an organization recover as quickly as possible if an attack penetrates the network. Recovering data from backups, regaining control of workstations, and spinning up parallel devices are examples of solutions for a quick recovery. Another factor to consider is that the company under attack has as little downtime as possible. In this case, recovery may include resiliency measures and tools.
What is NIST 800-171 and Why is it Critical for Your Business to Follow
Generally, if your business falls under any of these categories, you will be liable to follow NIST 800-171 guidelines:
- Defense contractors
- Educational and/or research institutions that handle federal data
- Financial and health service organizations
- Telecommunication service providers
NIST 800-171 is one of over 200 publications forming the CSF. It outlines the requirements that defense contractors must follow to protect Controlled Unclassified Information (CUI).
The NIST 800-171 guidelines reviews a series of cybersecurity requirements your business is required to follow in order to qualify for specific Department of Defense (DOD) contracts. If a business fails to meet the NIST 800-171 security requirements, it will not be considered secure enough to handle delicate government information.
The objective of NIST 800-171 is to guarantee a baseline of cybersecurity is in place, which applies to all government contractors and organizations that manage sensitive federal data. If your business meets these standards, then you can be confident that you have a strong Security System Plan (SSP) in place.
Key Differences Between NIST CSF and NIST 800-171
Considering that NIST 800-171 makes up part of the framework for NIST CSF, there are key differences that set them apart.
The NIST 800-171 publication focuses on cybersecurity requirements that potential DOD contractors must meet to receive access to government contracts. Failure to meet the minimum-security standards outlined in this publication can result in the loss of contracts.
Specifically, the publication applies to non-federal information systems that either store or transmit controlled unclassified information (CUI). In contrast, CSF is a holistic cybersecurity framework. Meeting CSF requirements means your business will easily remain in compliance with other frameworks, like PCI, DSS, and SOX.
Lastly, NIST CSF is completely voluntary as opposed to NIST 800-171, which is mandatory if you would like your organization to be eligible for DoD contracts.

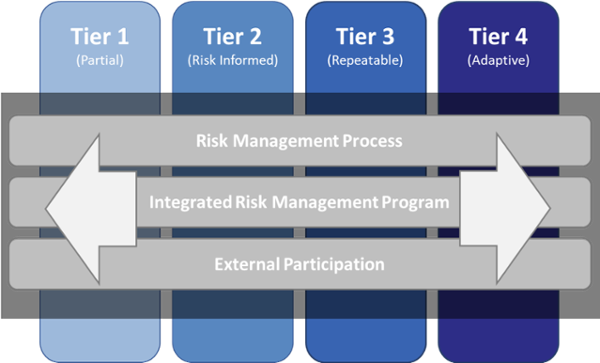
Tiers of NIST
NIST Cybersecurity Framework Tiers help categorize your company's potential risks based on size and industry, along with analysis of the processes you use to mitigate risk.
As put by NIST, the four Tiers "describe an increasing degree of rigor and sophistication in cybersecurity risk management practices" (nvlpubs.nist.gov).
Let's take a closer look at the different Tiers. Which one does your organization identify with the most?
Tier 1 - Partial
Companies in Tier 1 are just beginning their cybersecurity journey. At this point, the organization most likely has informal practices in place, and there is little awareness among the employees and stakeholders about these data security practices. There is no formal cybersecurity coordination in the organization to combat potential breaches.
Tier 2 - Risk-Informed
Tier 2 organizations have started to formalize their cybersecurity efforts. You may have secured the seal of approval from management on processes and prioritization, but an organization-wide coordinated effort has yet to be launched.
Though adequate resources have been allocated to the efforts, they haven't quite gotten off the ground.
Tier 3 - Repeatable
If your company falls into the Repeatable Tier, you have established formal policies that define risk management, and you have implemented practices to address these cybersecurity risks.
Your company’s processes are regularly reviewed and updated to ensure you are prepared in case of a breach. You have earned buy-in from your entire organization, and you have regular, formalized coordination on putting cybersecurity best practices into action.
Tier 4 - Adaptive
These organizations have refined the adaptive approach to cybersecurity management. Their practices constantly adapt based on past experiences and future predictions. Cybersecurity best practices are ingrained in the organization’s culture, and all stakeholders are actively working toward better security outcomes.
Why should you comply?
NIST is not a dictatorial set of standards. There are many benefits available to all kinds of organizations, regardless of the type of business they conduct, that provide value in data security.
There are damaging consequences to not being compliant that can be detrimental to your business. On the other hand, your business will have a competitive advantage when complying with NIST standards.
Consequences of Non-Compliance
Consequences of non-compliance with NIST standards are:
- Loss of Business: When your data is compromised, your status as a government contractor could be in jeopardy. Your business could lose a significant number of clients and miss out on future revenue.
- Impacted Productivity: Your company's productivity levels, in the case of a serious data breach, could be greatly impacted. As soon as a threat is on the radar, the top priority is to report it and fix the situation. This diverts resources from other important tasks to the emergency at hand - dealing with the branch.
- Tarnished Reputation: Businesses will not entrust sensitive data to a company with a reputation for reckless data security policies. If you fail to comply with NIST standards, your company's reputation could be seriously damaged.
- Lawsuits or Criminal Charges: This is by far the most serious consequence of non-compliance. If it has been determined that negligence of security led to a breach, or your company knowingly put data at risk, you could be subject to criminal charges. Your organization could face fines and breach of contract lawsuits.
Competitive Advantage
By getting aligned with NIST standards, it places your business way ahead of the competition. Companies want to know that they are dealing with a contractor or subcontractor that is authorized to protect their data.
If you can guarantee both NIST compliance and Controlled Unclassified Information (CUI) protection, and a competitor cannot, the bid will almost certainly go to you.
Check out our infographic on the "5 reasons why security compliance is important".
Datalink Can Help
Nist Compliance is a simple addition to your company's network. Without knowing why NIST helps, your organization may face problems down the line.
To ensure your network is robust and effective, you can conduct an Information Security Gap Assessment to identify areas of weakness within your network security controls.
Datalink Networks helps your team conduct this analysis based on your industry-standard security framework, including NIST and many others. Our team of experts will evaluate your staff and IT process to assess your environment.
After this evaluation, the team will provide a strategic roadmap to accomplish all information security requirements and find the vulnerabilities within your IT security infrastructure.
Today's information gaps turn into tomorrow's perilous chasms. Please contact us today for a free security audit from an IT expert!



.webp?width=300&name=NIST%20Compliance%20Blog%20Graphic%20(1).webp)