As cyber threats become more complex, businesses are seeking robust cybersecurity solutions to protect their digital assets. One significant response to this challenge has been the remarkable growth of Managed Security Services (MSS).
These services play a pivotal role in helping organizations fortify their cybersecurity posture. In this context, one key aspect that has gained prominence is the adoption of SOC 2 Compliance audits.
In the following article, we will delve deeper into the growth drivers of Managed Security Services and the specific reasons why undergoing a SOC 2 compliance audit is imperative in today's cybersecurity landscape.
Growth of Managed Services Since 2020
The growth trajectory of managed services has been nothing short of extraordinary since 2020. Businesses are increasingly recognizing the strategic advantages of outsourcing their IT management to MSPs.
According to Fortune Business Insights, the market size of global managed services was valued at $255.86 billion in 2022 and it is projected to grow from $283.90 billion in 2023 to $671.14 billion by 2030. This indicates the exponential growth of managed services across all sectors.
Factors such as the rise of remote work, increased cyber threats, and the need for scalable and resilient IT solutions have fueled this growth. As organizations continue to digitize their operations, the demand for comprehensive and reliable IT support provided by MSPs is expected to surge. This trend is indicative of a broader shift in how businesses view and prioritize their IT infrastructure, acknowledging the role of MSPs as indispensable partners in their success.
How do MSPs Help Business with IT?
Managed Service Providers play a pivotal role in empowering businesses by shouldering the burden of IT management.
Managing one's technology can be a full-time job, and small to mid-sized businesses often don't have the resources to hire an entire team to do it for them. Therefore, this can be a major challenge for the SMB community to keep their IT running smoothly.
The solution is outsourcing the task to an MSP, who act as strategic partners by offering proactive monitoring, maintenance, and problem resolution to ensure the seamless functioning of IT systems. This not only enhances operational efficiency but also minimizes downtime, a critical factor in today's fast-paced business environment. The collaborative nature of the MSP-client relationship fosters a proactive approach to IT management, preventing issues before they escalate.

Cyber Crime Today for SMB/SME Business
According to Business News Daily, 43% of data breaches involve small business victims.
According to Business News Daily, the average data breach cost for businesses with fewer than 500 employees is $2.98 million.
According to Security Magazine, nearly half (47%) of businesses with less than 50 employees do not allocate a budget for cybersecurity measures.
The Consequences of a Cyber Attack for SMB/SME Businesses
The consequences of a cyber-attack on SMBs/SMEs can be severe, encompassing financial losses, operational disruptions, legal repercussions, and damage to reputation. Data breaches can result in the loss of customer trust, which is often challenging to regain.
In an interconnected business landscape, the fallout from a cyber-attack extends beyond the immediate victim, affecting partners and clients, emphasizing the critical importance of robust cybersecurity measures.
Why do Cyber Criminals Target Managed Service Providers?
MSPs have become prime targets for cybercriminals due to the valuable data they possess and their interconnected relationships with multiple clients. Successfully infiltrating an MSP can provide cybercriminals with a gateway to multiple businesses, amplifying the scale and impact of their attacks. From an attacker's perspective, this is significantly easier than having to break into each business's network individually.
They often manage critical infrastructure for their clients, making them high-value targets for ransomware attacks where the potential for extortion is significant. In addition, some MSPs, particularly smaller ones, might not have the same level of cybersecurity defenses as their larger clients. Cybercriminals may see them as a softer target, making it easier to compromise their systems and gain unauthorized access.

SOC 2 Audit: What is it and why is it necessary?
Despite efforts by IT security professionals to counter threats, a report from Juniper Research anticipates that more than 33 billion records are expected to be stolen by cybercriminals in 2023 alone. To prevent this from happening, a SOC 2 audit is heavily recommended.
A SOC 2 (Service Organization Control 2) audit is typically performed by independent auditing firms or third-party service organizations. These auditors assess and validate the effectiveness of an organization's information security policies and practices. They focus on the security, availability, processing integrity, confidentiality, and privacy of the data handled by the organization.
SOC 2 audits are commonly used for technology and cloud computing organizations, as well as those that handle sensitive client information. The audit is based on the AICPA (American Institute of Certified Public Accountants) Trust Service Criteria.
By obtaining SOC 2 Compliance, MSPs can assure their clients that they have implemented effective security and privacy measures to protect their data. Successfully passing a SOC 2 audit demonstrates a commitment to the highest standards of data security and privacy.
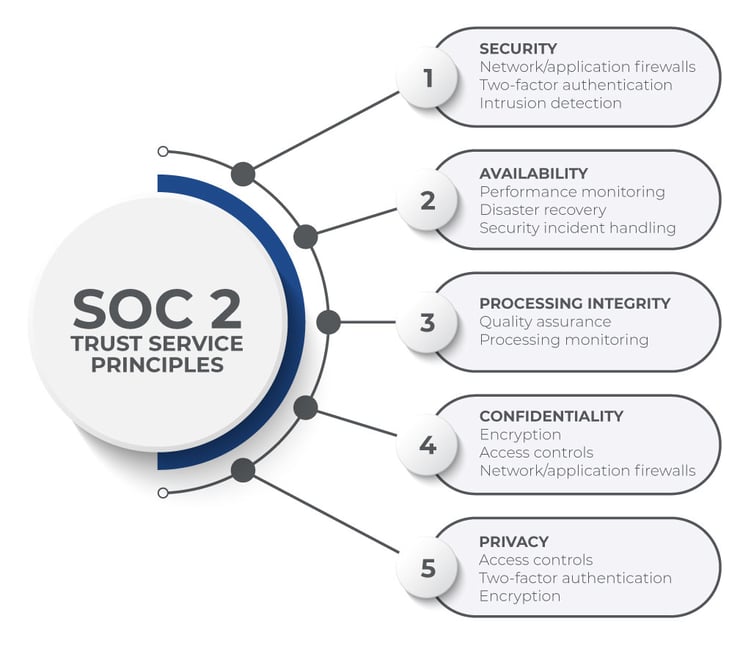
Why is it Important to Have this Examination?
SOC 2 Compliance is crucial for MSPs for several reasons:
-
Trust and Credibility: SOC 2 Compliance demonstrates that an MSP has implemented robust controls and safeguards to protect client data. This helps build trust and credibility with clients, as they can be confident that their sensitive information is secure.
-
Competitive Advantage: SOC 2 Compliance sets MSPs apart from their competitors who may not have undergone the same level of scrutiny. It can be a valuable differentiator when clients are evaluating service providers.
-
Regulatory Compliance: Many industries, such as healthcare and finance, have specific data security regulations that require service providers to adhere to certain standards. SOC 2 Compliance helps MSPs meet these regulatory requirements and avoid potential penalties or legal issues.
-
Risk Management: SOC 2 Compliance helps MSPs identify and mitigate potential risks related to data security and privacy. By implementing the necessary controls and processes, MSPs can proactively address vulnerabilities and protect their clients' data.
Potential Risks of Working with a Firm that does not have a SOC 2 Examination
Without the assurance of a thorough audit, there's uncertainty about the effectiveness of the firm's security controls. This lack of transparency can lead to vulnerabilities that cybercriminals may exploit, jeopardizing not only the security of sensitive data but also the overall stability and reputation of the businesses relying on these services.
Some potential risks include:
-
Data Breaches and Loss of Confidentiality:
Organizations that lack a SOC 2 certification may have inadequate security controls, making them susceptible to data breaches.
According to a study by IBM, the average cost of a data breach in 2022 was estimated to be $4.24 million. Without the rigorous evaluation provided by a SOC 2 audit, there's a heightened risk of unauthorized access to sensitive information, leading to financial losses and damage to a company's reputation. -
Operational Disruptions and Downtime:
A lack of comprehensive security controls increases the likelihood of operational disruptions. Cyberattacks such as ransomware can halt business operations, causing significant downtime.
According to a report by Cybersecurity Ventures, the global damage costs from ransomware attacks are projected to reach $265 billion by 2031. Working with a firm that hasn't undergone a SOC 2 examination exposes businesses to the potential of extended downtime and its associated costs. -
Regulatory Compliance Challenges:
Industries across the globe are becoming increasingly regulated, with data protection laws such as GDPR and HIPAA imposing strict requirements on how organizations handle sensitive information.
Engaging with a security firm without a SOC 2 certification may lead to compliance challenges, resulting in legal consequences and financial penalties. A SOC 2 audit helps businesses demonstrate compliance with industry standards, fostering a secure and regulatory-compliant environment. -
Reputational Damage:
A data breach or security incident can have lasting effects on a company's reputation. According to a survey by PwC, 45% of consumers said they would abandon a company following a data breach.
Without the validation provided by a SOC 2 examination, businesses risk losing the trust of their clients and stakeholders. The damage to reputation can have long-term consequences, impacting customer retention and new business opportunities. -
Inability to Attract Partnerships and Clients:
In an interconnected business landscape, companies often collaborate with partners and clients. However, firms without a SOC 2 certification may find it challenging to attract reputable partnerships.
Many businesses now prioritize working with security-conscious providers to mitigate the risks associated with third-party relationships. Without a SOC 2 audit, firms may struggle to secure partnerships, limiting their growth potential.
Concluding Thoughts: Act Now with SOC 2 Compliance
SOC 2 compliance stands as a crucial imperative for MSPs in safeguarding not only their own integrity but also the resilience of the SMBs they serve.
Cybercriminals recognize the centrality of MSPs, making them attractive targets for attacks. A breach in an MSPs security could have cascading effects, compromising the security of multiple SMB clients. SOC 2 compliance, with its emphasis on stringent security controls, not only mitigates the risks associated with such attacks but also ensures MSPs are well-equipped to fortify the cyber defenses of the SMBs that rely on them.
In essence, SOC 2 compliance is an indispensable investment in the collective resilience of MSPs and their SMB clients against the escalating threat landscape of cybercrime.
Contact us today to learn more about SOC 2 Compliance benefits and how Datalink Networks can help your organization.
Also, check out our press release diving into the details of our Type 2 SOC 2 Audit with A-Lign Assurance Firm.



