Update: 6/2/2023
AI and ChatGPT Attacks Using Microsoft Account Security Alerts
Cyber criminals are using AI and ChatGPT attacks to create fake Microsoft account security alerts that trick users into giving away sensitive information. These sophisticated attacks use machine learning algorithms to generate convincing messages that appear legitimate.
One of the most common types of AI and ChatGPT attacks is phishing emails, which attempt to lure users into clicking on a link or downloading an attachment that contains malware. The attackers often impersonate well-known companies such as Microsoft, making it difficult for users to distinguish between genuine and fraudulent messages.
Another type of attack involves creating a fake login page that appears similar to the official Microsoft website. Once users enter their credentials, they unwittingly provide access to their accounts for cybercriminals who can then steal personal data or launch further attacks.
The use of AI in these types of attacks makes them particularly dangerous because the technology allows attackers to quickly adapt their tactics based on user behavior. As such, it is essential that organizations take steps to protect themselves against these evolving threats by implementing robust security measures and educating employees on how best to identify and avoid phishing scams.
How cyber criminals are using AI spoof Microsoft account alerts to get your information
It is crucial for individuals and organizations to stay vigilant against AI and ChatGPT attacks using Microsoft account security alerts. Cybercriminals are constantly seeking new ways to trick users into revealing their sensitive information, and the use of AI technology has made these attacks more sophisticated than ever before.
To keep your organization safe from phishing attacks, it is important to educate employees about the risks of opening suspicious emails or clicking on links within them. Additionally, enabling multi-factor authentication can add an extra layer of protection against unauthorized access.
As technology continues to evolve at a rapid pace, it's vital that we continue to improve our cybersecurity measures in order to stay one step ahead of cybercriminals who are always finding new ways to exploit vulnerabilities. By staying aware and following best practices for online safety, we can help ensure that our personal information stays secure.
Tips to keep your organization safe from Phishing Attacks
Phishing attacks remain one of the biggest cybersecurity threats facing organizations today. These attacks are designed to trick employees into divulging confidential information or downloading malware onto their devices. While many organizations have implemented strong security protocols, phishing attacks continue to be successful due to human error.
One way to prevent these attacks is through employee education and training programs. By teaching employees how to spot a phishing email, they can avoid falling victim to an attack. For example, employees should avoid opening emails from unknown senders or clicking on suspicious links.
Another strategy is implementing multi-factor authentication (MFA) across all accounts and devices. MFA adds an extra layer of security by requiring users to provide additional verification beyond just a username and password.
Organizations should also regularly update their software and systems with the latest patches and fixes. This ensures that any vulnerabilities are patched up before hackers can exploit them.
It's important for organizations to create a culture of security awareness among employees. Encourage them not only to follow best practices but also report any suspicious activity immediately so that IT teams can respond promptly.
By following these tips, your organization can significantly reduce the risk of falling prey to a phishing attack - keeping your data secure at all times!
Have you received a Microsoft Account Security Alert from a questionable email? Depending on the sender, clicking the attached link could either secure your Microsoft account or lead to a security breach.
Before clicking the link, please read our blog on how to best act on any Microsoft Account Security Alerts you may receive. Below, we overview which links are safe, which are dangerous and how to safely navigate no matter who the sender is.
Is your Network Secure? Learn more about our complimentary security audits. Datalink Network security audits often find unused and/redundant services. Our finds not only make your network more secure, but save your organization money!
Microsoft Account Security Alert Phishing Attacks
Phishing Attacks
What is a phishing attack? It is a type of social engineering attack used to steal user data. The user data targeted is typically information like login credentials and/or credit card numbers.
Phishing attacks occur when an attacker impersonates a trusted contact and tricks their target into opening an email, text or instant message. Once the message is opened, the victim is then prompted to open a malicious link, leading to the installation of malware, or a link to an imitation site where the victim puts in their login info.
Depending on the attack, the results can be devastating. For individuals, an attack may result in unauthorized purchases, theft of funds or even identity theft.
Phishing is also used to penetrate corporate or governmental security perimeters. In this setting, phishing attacks are part of a larger attack angled to distribute malware inside a closed environment or gain access to privileged, secure data.
Example of a Microsoft Account Security Alert Attack
1) You receive an email that looks like this.
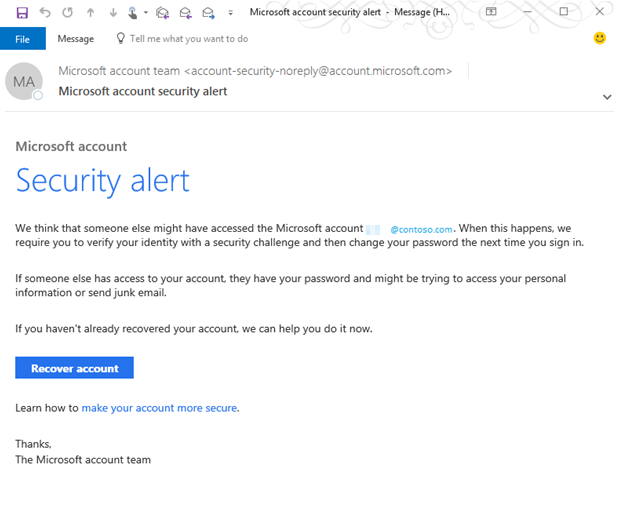
2) The email looks legitimate and the sender domain, “@account.microsoft.com” is a Microsoft property. Unfortunately, the sender domain has been “spoofed” and the emails original origin is actually unknown.
3) When you click the, “Recover Account,” link you are taken to a fake landing page designed to look exactly like Microsoft’s account recovery page. You’ll notice the landing page is not on Microsoft’s domain.
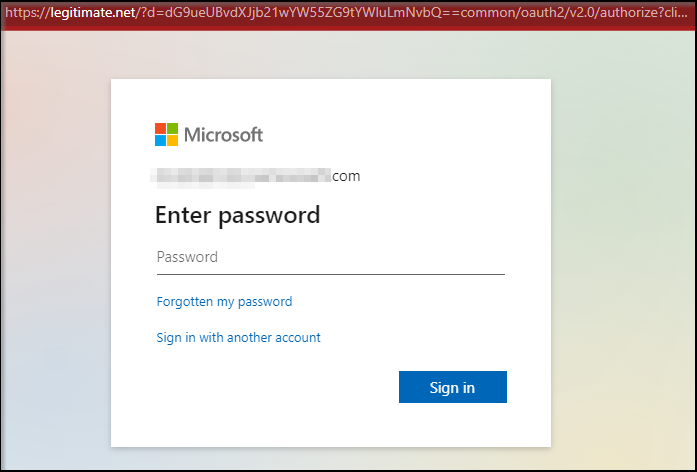
4) If you make the mistake of typing in your credentials, your Microsoft Account will be compromised.
5) This is just one type of Phishing Attack. Some attacks can happen simply by clicking the link (no other action needed).
6) Scammers and cyber criminals are not all stupid (African prince wanting to give you money). Many are talented web designers that can easily replicate a company's real login. With this attack, their objective is to trick you into actually thinking you are securing your Microsoft Account.
How to Prevent Microsoft Account Security Alert Attack
Don’t click! The effectiveness of this attack stems from copying a very real email that Microsoft actually sends. There is a chance this email is actually from Microsoft.
Here are the steps to make sure you don’t compromise your Microsoft account.
1) Check who the sender is. This does not help if the email has been, “spoofed,” but it can eliminate some attempts from Phishers who did not spoof the email. Spoofing lowers an email’s sender score, so some phishing schemes may not spoof to better their chances of making it to your inbox.
2) Check the button link. Go to the button, right click and, “copy link address.” Then, paste the URL into a text editor where you can review the link. Does it take you to a microsoft.com property?
3) Still, even if everything checks out, don’t click! Go to your Microsoft login like normal and try to login. Are you able to login?
4) If you’re able to login, the email was likely a scam email. If you are unable to login, follow the steps from Microsoft to recover your account. They will likely resend the original email. From there, repeat step #2. As long as the URL looks good, paste the URL into your browser and proceed in recovering your account.
Actual Microsoft Account Security Alert
Once again, the reason this particular phishing attack is so successful is because it copies an actual email sent by Microsoft. So, when would Microsoft send this sort of email?
1) If Microsoft detects a suspicious login attempt they may lock your account. This can be from an unknown IP address, a different machine, or a number of incorrect password attempts. When this happens, you may receive an email asking you to change your password or verify it was you attempting to login.
2) If an individual that is part of your license is compromised, Microsoft may freeze all account activity until every user is verified. This strategy can be used to, “stop the bleeding,” during a large, coordinated cyber attack.
3) If your Microsoft account is compromised or suspected to be compromised you may receive an email to your backup email asking you to change your password or verify recent activity.
In all of these scenarios the hope is to stop a cyber criminal before they are able to access too much data. However, many times Microsoft’s actions come too late and the damage is done.
Disaster Recovery and Continuity
Your business is a target. It may not happen today or tomorrow, but eventually a cyber criminal will try to access your most sensitive data.
It is imperative you have security systems in place and your staff is well informed on how to handle these attacks. Unfortunately, without professional security systems in place even networks with moderate security will be successfully penetrated.
To ensure your business continues to run smoothly, you must have a disaster recovery plan in place to allow your business to operate with continuity.
Downtime Cost Businesses
Did you know that one hour of downtime cost the average tech business between $9,000 and $70,000?
The main culprit of downtime is ransomware and/or human error.
Is your Network Secure? Learn more about our complimentary security audits. Datalink Network security audits often find unused and/redundant services. Our finds not only make your network more secure, but save your organization money!
Concluding
Microsoft Account Security Alerts can be both a real notification from Microsoft or a phishing attack from a cyber criminal. Having a workforce that is trained in how to verify the validity of the email is important to protecting your network.
The same steps described above should be used on any unexpected email. Don’t click links just because you are prompted! Make sure the link is taking you to a trusted, safe site.
Attacks are inevitable and it is imperative you have a disaster recovery plan in place in the event a cyber criminal is successful. Cyber crooks don’t have to win. A solid security system and recovery plan will limit any damage that can be done to your network.


