Did you know that nearly 1.2% of all emails sent are malicious, which translates to about 3.4 billion phishing emails daily. Extortion of over 33 million records is expected to occur by the end 2023 with a ransomware or phishing attack occurring every 11 seconds on average.
SlashNext found that link-based URLs, attachments and natural language messages in email, mobile and browser channels over six months in 2022 and found more than 255 million attacks —a 61% increase in the rate of phishing attacks compared to 2021.
Additionally due to the blurred lines between home and work, it creates a security nightmare for IT departments if safety protocols are being ignored by employees. Because no industry or organization is immune to these attacks it is critically important for all organizations to take preventive measures to both recognize, avoid, and report phishing emails attacks.
Read our ultimate guide to build your information security program!
The Impact of Phishing Attacks
According to Barracuda Networks, 3 out of 4 organizations are victim of a successful email attack. Only 2% of respondents said that email attacks had no impact on their organization. These staggering statistics showcase the devastating damage that phishing attacks can inflict on companies on a small or large scale. Because of this, it is incredibly important for your organization to recognize phishing attacks in order to keep your organization safe.
The overall impact of phishing attacks can include:
- Machines infected with malware/viruses
-Stolen log-in credentials and/or account takeover
-Reputational Damage
-Direct Monetary Loss
-Sensitive or confidential data stolen
The dangers of phishing can vary amongst businesses and organizations depending on the severity of the attack and the amount of data that is forfeited to hackers.
Types of Phishing Attacks to Avoid
(1) Whaling
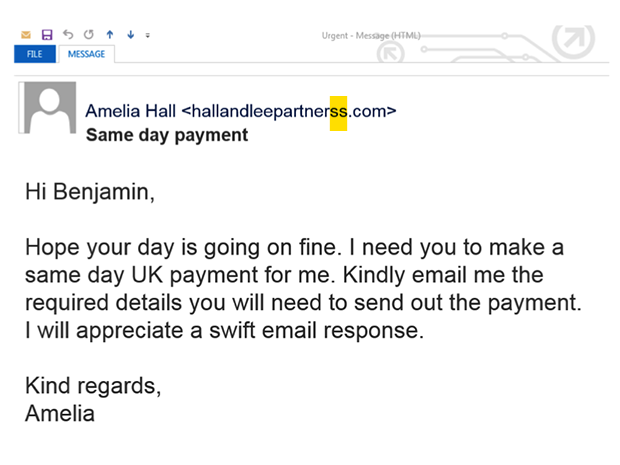
Whaling is a form of spear phishing and focuses on high value targets, such as C-Level employees. These emails are focuses on gaining access to company platforms or financial information to extort money. Unlike typical phishing or spear phishing scams, in which an attacker typically includes a malicious URL or attachment, whaling is a pure social engineering hack targeting relationships between employees, says Steve Malone, director of security product management at Mimecast.
Read about Microsoft security and Microsoft defender for business.
(2) Mass Campaigns
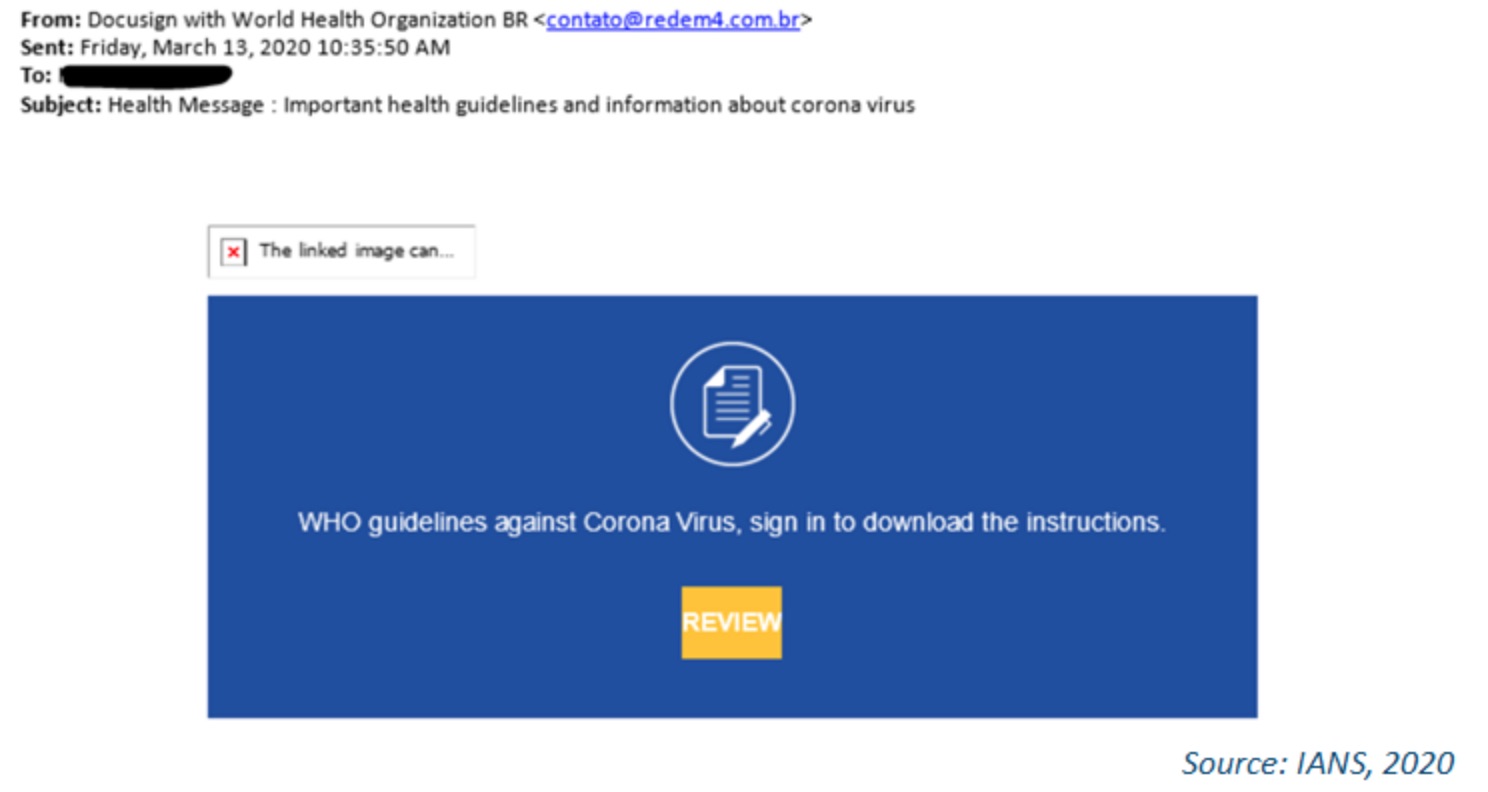
Through mass campaign, emails are sent to the masses from a fake corporate entity. Typically, these emails will insist that a password needs to be updated or credit card information is outdated. An example of these types of mass email campaigns is shown above.
In 2020, we saw an example of these email campaigns when targets received fraudulent emails encouraging them to donate to relief funds for either recent natural disasters or the COVID-19 global pandemic.
(3) Pretexting
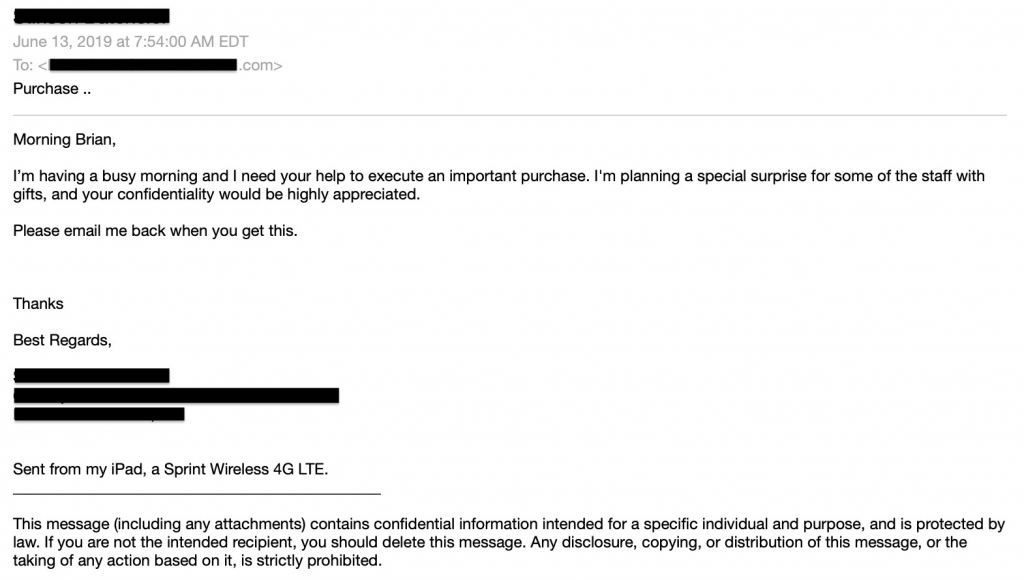
Unlike the previous phishing attacks, pretexting involves an attacker doing something via a non-email channel, such as voicemail, to set the expectation that they will be sending over something legitimate when in fact that email contains malicious content and links. To avoid becoming a victim of pretexting businesses can look into artificial intelligence anti-spear phishing technology that analyzes behaviors for signs of pretexting or malicious patterns.
How to Prepare for Phishing Attacks
Based on the success and proliferation of email-based attacks, your IT security team will need to stay focused on the evolutions of phishing threats. To prepare for and prevent phishing attacks, the adoption of managed services and email security software is a necessity. Likewise, by improving phishing awareness throughout your organization by using real-life simulation tools, is essential to ensure that every user is well trained to create a strong line of defense.
Interested to learn about the benefits of Managed Services? Read our complete guide here!
Need help finding the right email security software for your organization? Contact us today to see how Datalink Networks can help.





