In the year 2022, a total of 1802 instances of data breach came to light. These incidents cast their shadow over more than 422 million individuals, subjecting them to the repercussions of these breaches, encompassing data leaks and exposures. One effective strategy to bolster security within your establishment involves the activation of Group Policies. By harnessing the power of group policies in the right manner, your organization can elevate the safeguarding of users' computer systems, providing a strong line of defense against both internal vulnerabilities and external assaults. Subsequently, the advantages of implementing group policies will become evident, revealing how they contribute to your organization's well-being.
To fortify your organization's resilience against such adversities, embracing Group Policies emerges as a strategic imperative. By proficiently harnessing the capabilities of group policies, your company not only enhances the security of users' computer environments but also constructs a robust bulwark against insider hazards and external incursions. As this transformative approach takes root, the post-implementation landscape promises to unveil the manifold benefits that group policies bring to the forefront of your organization's security posture, ensuring a steadfast and fortified digital ecosystem.
Is your Network Secure? Learn more about our complimentary security audits. Datalink Network security audits often find unused and/redundant services. Our finds not only make your network more secure but save your organization money!
What is a Group Policy Object (GPO)?
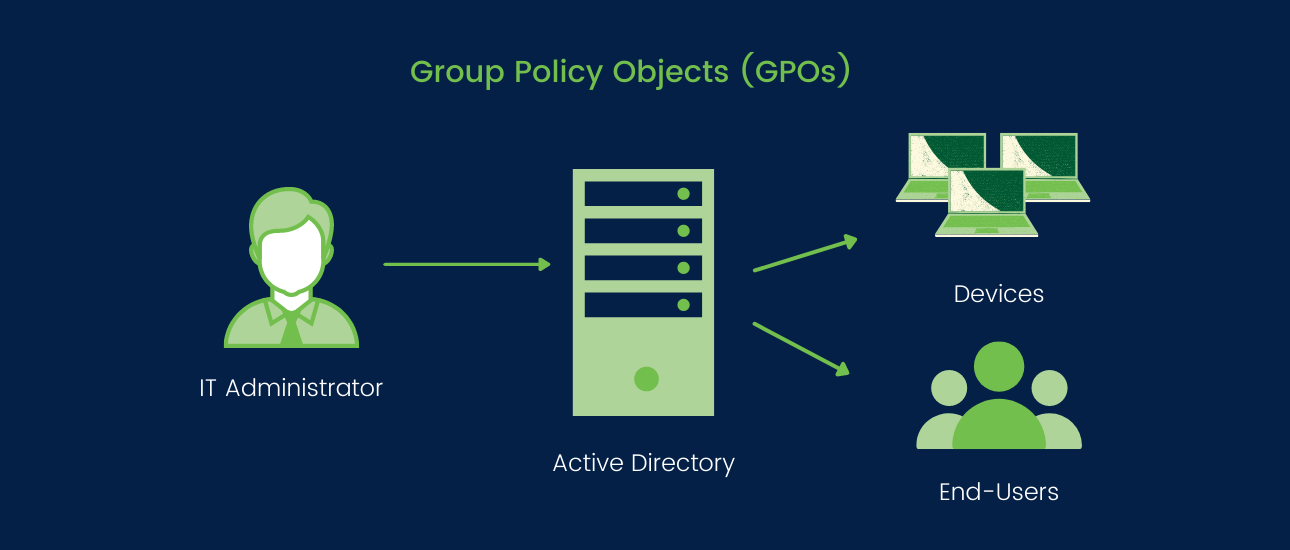
A Group Policy Object (GPO) in Microsoft Windows allows administrators to control settings for users and computers in a network. GPOs are used in Active Directory environments common in businesses. They group settings and policies for specific users, groups, or computers, enabling security enforcement, resource access control, software setup, and user experience customization. GPOs centrally manage configurations for many computers, ensuring network-wide consistency and security while simplifying administrative tasks.
AZURE GPO
Approximately two decades ago, Microsoft introduced Group Policy, which has since evolved into a prominent tool for the management and fortification of Windows desktop environments. Group Policy serves as the means through which administrators can bolster security measures, thus mitigating potential vulnerabilities that might otherwise expose the system to breaches. Administrators are granted the authority to leverage Group Policy in order to:
- Impose restrictions on access to the control panel.
- Modify the default name of the local administrator.
- Implement comprehensive disk encryption.
- Roll out configuration and registry settings.
Group Policy configurations are encapsulated within a Group Policy Object (GPO), which embodies policy settings both within the file system and the Active Directory. These GPOs can be linked to individual or multiple Active Directory containers, encompassing domains, sites, or organizational units (OUs).
What are the benefits of Group Policy Objects (GPOs)?
Incorporating Group Policy Objects (GPO) into your organizational framework can yield a range of advantageous outcomes:
-
Centralized Management: GPOs offer a centralized avenue for administering both computer and user settings, ensuring uniformity across the network.
-
Robust Security Enforcement: IT administrators gain the capability to apply stringent security protocols, such as compelling password policies and regular password rotations to counter susceptibility to compromise.
-
Enhanced Accessibility: Through features like folder redirection and offline files, users can access files even in cases of poor network connectivity, fostering seamless collaboration.
-
Consistent Computing Environment: Users can experience a consistent computing environment regardless of the workstation they use, promoting efficiency and familiarity.
-
Data Safety Net: By redirecting user files to a server location, regular backups mitigate the risk of data loss stemming from workstation failures, safeguarding vital information.
Disadvantages of Group Policy Objects (GPOs)?
While the advantages of utilizing group policies are considerable, certain drawbacks should be acknowledged:
-
Network Flexibility Constraint: GPOs can limit network flexibility, as they can only be applied to users or computers, restricting their adaptability for broader settings or reacting to dynamic environmental changes such as network disconnections.
-
Maintenance Complexity: Despite their organizational benefits, GPOs can be challenging to maintain. The absence of a built-in filter option to locate specific settings complicates the task of identifying and resolving issues within existing configurations.
-
Sequential Processing Impact: The sequential execution of GPOs, as discussed earlier, can impede user logon processes if configurations require an extended period to implement.
-
Lack of Audit Trail: While GPOs excel at establishing security policies for end-users, they lack a comprehensive audit system. This deficiency makes it difficult for IT administrators to track when changes were made or who initiated them, potentially hindering transparency and accountability.
It's essential to weigh these limitations against the benefits to make informed decisions when implementing GPOs within your organization.
Type of Group Policy Objects (GPOs)
When learning about GPOs, there are three main types that you should be aware of:
1. Local Group Policy Objects
Local group policy objects exist by default on all Windows computers and are utilized when IT admins need to apply policy settings to a single Windows computer or user. These types of GPO's only apply to local computers and to the users that log on to that computer on-site.
2. Non-local Group Policy Objects
Unlike local GPO's, non-local group policy objects require your Windows computers and users to be linked to Active Directory objects, sites, domains, or organizational units. This means that non-local GPO's can apply to one or more Windows computers and users.
3. Starter Group Policy Objects
Starter GPOs are templates for group policy settings. These templates enable IT, administrators, to pre-configure a group of settings that represent a baseline for any future policy to be created.
Examples of a Group Policy Object (GPO)
GPO's can be used in numerous ways to enhance security within your organization. Below we have outlined some examples of how your organization can use GPO's:
-
IT Admins can use GPOs to define which network-connected printers or devices appear available on a user setting if that used if log into a specific Active Directory OU log onto the domain
-
IT Admins can use GPOs to determine the home screen a user will see once that user logs on to their device or internet browser.
-
IT Admins can use GPOs to improve security within your organization by enforcing CTRL+ALT+ DELETE to be executed every time a user logs in. This is to prevent hackers from logging into the domain remotely.
Group Policy vs. Azure Policy
The main difference between group policy and Azure policy is the architecture that it is based on.
Traditional Group Policy is based on an architecture that is for users and computers within an Active Directory, however, within the cloud and Azure policy user accounts are managed under the Azure Active Directory.
This connection into the Azure AD allows for:
-
Management of devices via Microsoft Endpoint Manager and Microsoft 365 Business.
-
Device-based conditional access policies to be applied based on whether the device is known to Azure AD
-
Supporting single sign-on and access to Microsoft Cloud resources by logging in to Azure AD
Some other notable key differences between group policy and Azure policy is that the latter includes settings for Azure subscriptions, settings for Azure resources, and settings for "in-guest configuration".
How do Group Policy Objects (GPOs) work?
Group Policy Objects (GPOs) serve as a framework to manage computer and user settings in Windows networks. They're essential in Active Directory environments, allowing administrators to centrally regulate system behavior, security, and functionality. Here's a concise breakdown of how GPOs function:
1. Creation and Configuration: Admins use the Group Policy Management Console (GPMC) to form GPOs. Each GPO comprises policies and settings dictating computer and user behavior. These include security protocols, software rules, access permissions, etc.
2. Scope Assignment: GPOs link to specific Active Directory containers (domains, OUs, sites), dictating their impact. For instance, an OU-linked GPO affects users and computers in a department.
3. Hierarchy and Inheritance: GPOs follow a hierarchy, with settings inherited downward. Various GPOs' settings can combine to affect one user or computer.
4. Processing: At logon/startup, GPOs linked to relevant containers are processed sequentially, considering local, site, domain, and OU-based GPOs. Filters determine applicability.
5. Policy Application: Processed GPOs' policies influence user sessions or computer configurations, affecting security, appearance, software, and access.
6. Policy Refresh: GPOs refresh periodically to ensure current configurations, reflecting updates or changes.
7. Group Policy Replication: GPOs are stored in Active Directory and domain controllers, syncing changes for network-wide consistency.
8. Feedback and Control: Admins monitor via tools like Event Viewer and Group Policy Results, also controlling enforcement and settings.
Summarily, GPOs streamline centralized configuration for computers and users in networks. They ensure consistency, security, and effective management while accommodating flexibility through hierarchy and inheritance.
Is your Network Secure? Learn more about our complimentary security audits. Datalink Network security audits often find unused and/redundant services. Our finds not only make your network more secure but save your organization money!
Next Steps? Contact Datalink Networks
If your in-house team requires assistance, Datalink Networks is always available to help guide your team on how to implement GPOs into your MCC and how to better secure your organization. Get connected to our team today by submitting the form below.



