With a huge shift in culture from in-office work to remote-based work, cybersecurity has never been more important. In fact, within just December of 2020, there have been several major cybercrimes on companies, such as SolarWinds and FireEye.
This affected large organizations like Microsoft and government entities, like the US Treasury. These cyberattacks are particularly concerning as, “this threat poses a grave risk,” to government on every level, as well as private organizations, based on a statement made by CISA, the Cybersecurity and Infrastructure Security Agency.
So, what can your organization do to ensure that you are as safe and secure as possible? Keep reading to learn our top 5 cybersecurity rules for you to live by.
Read our article about top data breaches and Cybersecurity attacks in 2021.
1. Protecting your Personal Data
Performing effective security practices against cyberthreats in the workplace stems from how you apply them in your personal life. Take a moment to reflect on all the ways you keep yourself safe online on a day-to-day basis.
As consumers, we are constantly receiving emails, phone calls, and messages from companies we shop from regularly. In some instances, hackers disguise themselves as reputable businesses and attempt to steal information that could put a company at a huge loss.
It's crucial to exercise caution against these hackers in your workplace the same way you would approach their efforts in your daily life.
Email Hacking Attempts to Compromise Your Business
In 2018, "business email compromise (BEC) accounted for just under $1.3 billion in losses," according to the Forbes Technology Council. That number has grown at an alarming rate in the last couple of years and will continue to do so. To some, this is a given, but it's very important to never share sensitive company information or leak any data.
With over 91% of cybersecurity attacks beginning from phishing emails, email security has become widely recognized as a crucial part of any IT environment. You will encounter phishers and potential scam emails that try to get you to click a fake link that may be embedded with malware and viruses.
The strongest plan of action (to prevent this from happening to you or your coworkers) is to authenticate information within the email, like the subject line/email headers and domain name. If those are misspelled or contain any unusual symbols, they are usually not legitimate.
Check out our complete guide to email security with a top solution comparison guide.
Password Protection/Authentication
When creating company passwords, a general rule of thumb is to make them as complex as possible, and to never opt in to save your password. A strong password will contain at least 10 characters, including symbols, numbers and capital letters.
Cyberthieves can easily acquire access to your company network through a simple password. That's why most companies will require two-factor authentication to log in, whether it be sending a temporary code to your mobile phone, or requiring you to download the Authenticator app.
We suggest changing passwords as frequently as possible and removing old users who no longer work for your company, as they may still have access to your platforms online.
![]()
2. Know your Security Posture
Security posture is an organization’s overall security status; based on software, network, services, and more. Understanding your organization’s security strengths and weaknesses allows you to make informed decisions regarding your cybersecurity plan and to fill any existing gaps.
By regularly checking your security posture and patching holes as needed, you are more likely to remain secure from cybercriminals looking for easy access into your network.
Assessing your Network Security
So, how do you determine your security posture? Datalink Networks offers a Free Network Security Assessment, which identifies weaknesses and provides you with a security report card to increase security and lower risk.
Additionally, you can schedule routine penetration testing. This is a form of ethical hacking which identifies security gaps and an organization’s ability to respond to threats. By performing a pen test on your organization’s network, you go through the hacking process cybercriminals use to gain access - so you can ensure that all avenues become dead ends.
![]()
3. Increase Protection
Understanding your security posture is only half the battle. Once you identify your weaknesses and gaps in security, the next step is to fill those gaps to increase protection. This is especially important as cybersecurity breaches have increased by 67% in the past 5 years.
Barriers to Security
Leveraging several different types of protection such as: email security, firewalls, and antivirus software, creates stronger barriers for your organization. These different forms of protection work like a patch-quilt blanket, ensuring that every portion of your network is secure.
These barriers carry less vulnerability and exposure, blocking out cybercriminals and keeping them at bay. Additionally, all software should be updated regularly, as the previous version sometimes carries bugs that can interfere with their effectiveness. This can also increase the stability of the software, provide new features, and make the overall user experience smoother.
Read about cybersecurity for small to medium businesses.
Use Third-Party Controls
Another huge area of concern for a potential data breach is how you manage employee access within the company. It's quite common for these breaches to originate from someone on the inside, and this is why organizations should consider limiting who has access to important client information.
If an employee is responsible for accessing the client database, be sure he/she strictly abides by company rules around storage and the use of delicate information. If one is responsible for safeguarding the hard or soft copies, ensure he/she takes the role seriously, because that individual is the main defender against illegitimate third-party groups.
Additionally, you should consider any former employees who are no longer with the company, or any consultants that may still have access to the computer network. It's crucial to regulate any lingering third-party access and always remember to terminate their access when their job is done.
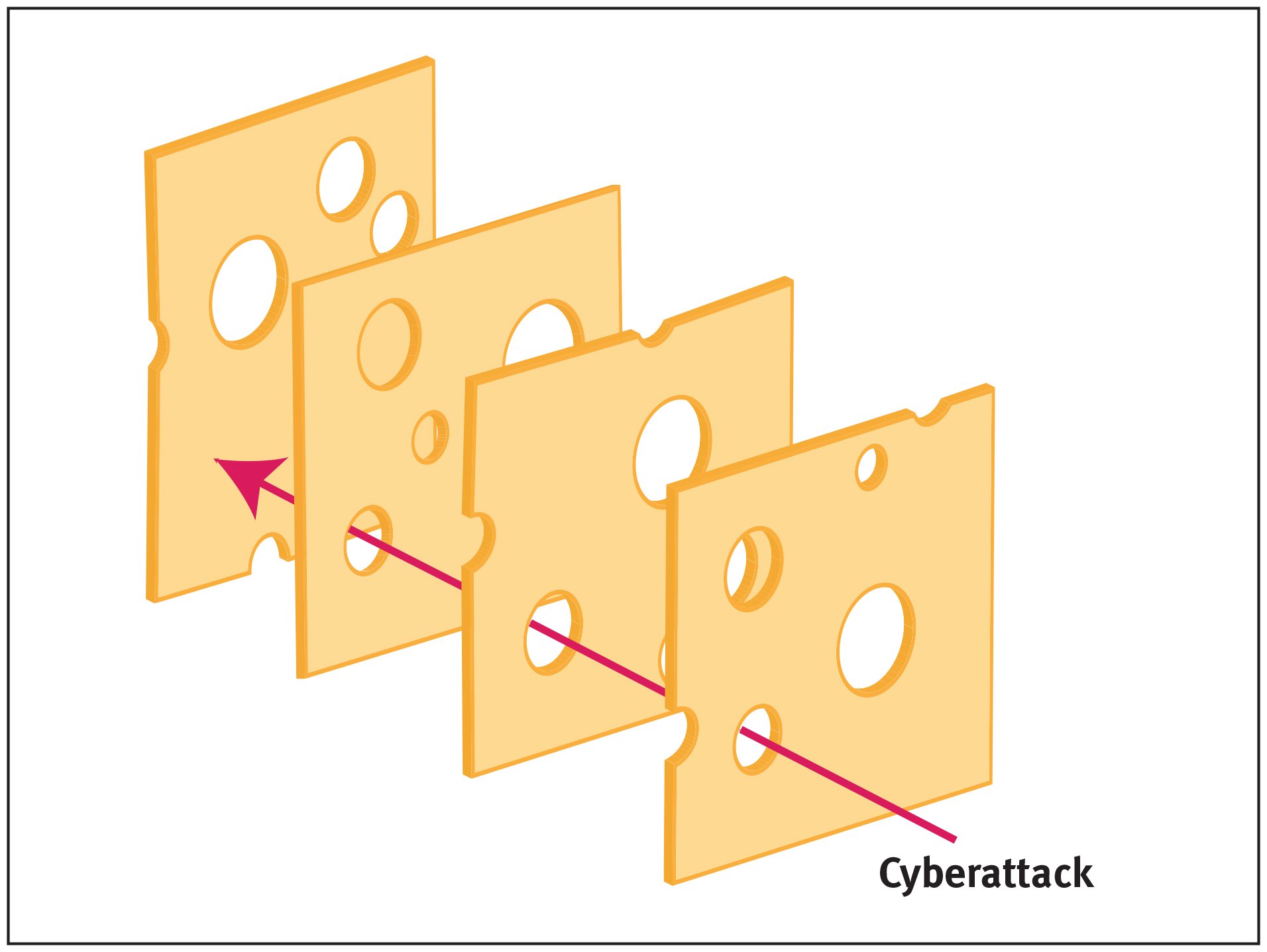
4. Have a Backup and Recovery Plan
While we hope you never need it, it's important that your organization has a comprehensive backup and recovery plan. This is essential for any business to have; in case a cybercriminal infects your network with malware, or an employee deletes sensitive data.
This is primarily important, as ransomware attacks cause an average of over 16 days of downtime, and average downtime costs up to $11,600 per minute. Of course, ransomware isn't the only looming cyberthreat organizations are currently facing. Software supply-chain attacks are also a significant threat, along with API-based application threats and modern fifth-gen bots.
Benefits of Working with a Managed Service Provider
By having a backup and recovery plan, you can significantly decrease downtime, saving your organization time and money, and protecting yourself from losing important data. You can either work with an IT vendor to create and deploy a plan that your organization manages, or you can work directly with a Managed Service Provider, who will also monitor your network and act if a threat arises.
Working with a Managed Service Provider, like Datalink Networks, will provide the highest value, as we can prevent attacks before they occur with 24x7x365 network security monitoring services.
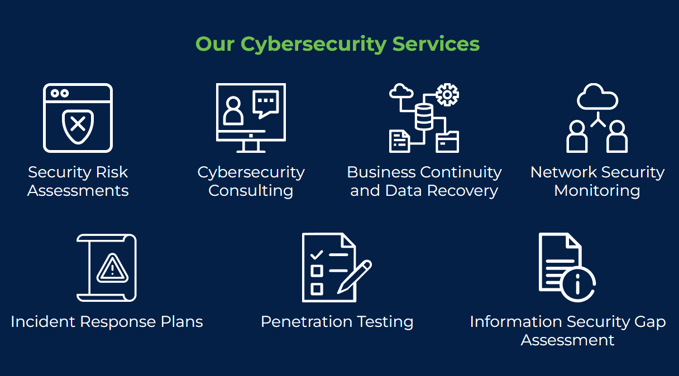
Here are some cybersecurity services you can take advantage of with Datalink Networks as your Managed Service Provider:
5. Policies and Training
Did you know that insider threats have increased by 47% over the past two years, and more than two thirds of them are caused by employee negligence? This negligence is often shown through emailing sensitive information, using a personal email instead of a work email, falling for phishing attacks, and losing work devices.
To mitigate this risk, create a company-wide set of cybersecurity policies and procedures, and train your staff on them. These policies can include:
-
- Multi-factor authentication requirements
- Password policies
- Protocol for payment changes
- Social media policy
Implementing Security Practices
By training your staff on proper cyber-procedure and the importance of adhering to policies, you will protect your organization significantly. Training your employees on the tell-tale signs of phishing emails so they can recognize and ignore them will help keep your organization from falling victim.
Your employees can either be your biggest asset or your largest downfall. It's important to give employees the tools they need to understand the security risks, so they don't become negligent.
Click here to read about the global challenge of cybersecurity.
Instilling Long Term Behavioral Change
The majority of training programs that companies use aren't designed to establish long term behavioral change within an organization. Employees normally watch extensive informational sessions on topics, like harassment and racial discrimination (to name a couple), which do not engage their interest.
Narratives in online training have proven to be quite powerful tools for learning. When integrating this tool into your programs, it's strategic to discuss the ramifications of real-life cyber-attacks with your employees. Showing them in a visual format can also have more of an effect on their learning.
Digital Storytelling as a Tool
As far as training programs in cybersecurity awareness go, there's still room for growth in creating engaging, interactive content that employees can get excited about. There are many great digital formatting tools employers can get their hands on nowadays to create fun, virtual environments for learning.
The over-used video, followed by a quiz format is not doing the job anymore. Some good examples of digital storytelling websites are: Capzles, Comic Master, Slidestory, and ZooBurst - which allows you to create your own 3D popup books.
Training programs should be focused on long-lasting effectiveness, in addition to addressing a serious internal issue. This is the only way to ensure that your employees will take away something of value and continue to practice those policies on a consistent basis.
How Cybersecurity Fits In
To ensure effective cybersecurity training, you need to captivate your employees by making sure they will benefit from participating. As a manager or higher-up position in the company, you can do so by receiving buy-in at every level.
Some companies will offer their whole staff friends and family use rights. As a result of providing training for employee use for family protection, you are keeping your company safe because the topic is now valuable to your employee.

Conclusion
If your organization cannot operate because it is under a ransomware attack or responding to a major data breach, your other business activities will be sidelined. New, inventive threats from hackers, the sinister rise of malware-as-a-service, and intensifying business and regulatory requirements demonstrate that cybersecurity is one of today’s top business challenges.
Next Steps? Contact Us Today!
The cybercrime time-bomb is ticking for small and medium-sized businesses (SMBs). 43% of all data breaches involves SMB's - don't let your organization fall victim to an attack. Contact Datalink Networks today for a complimentary security audit.




