With cybercrime on the rise and 95% of breaches coming from human error, organizations need to be more careful than ever with their overall security. As some employees remain at home and others begin coming back into the office, you need to ensure that the devices they use to access work data are secured and compliant. Do you have a plan to wipe data if an employee's laptop is stolen or lost? What if they start accessing work documents on a personal laptop with minimal security? If you don't already have a solution in place to solve these potential problems, Mobile Device Management is a great place to start.
Top 6 MSP red flags! Switch to another Manager Service Provider.
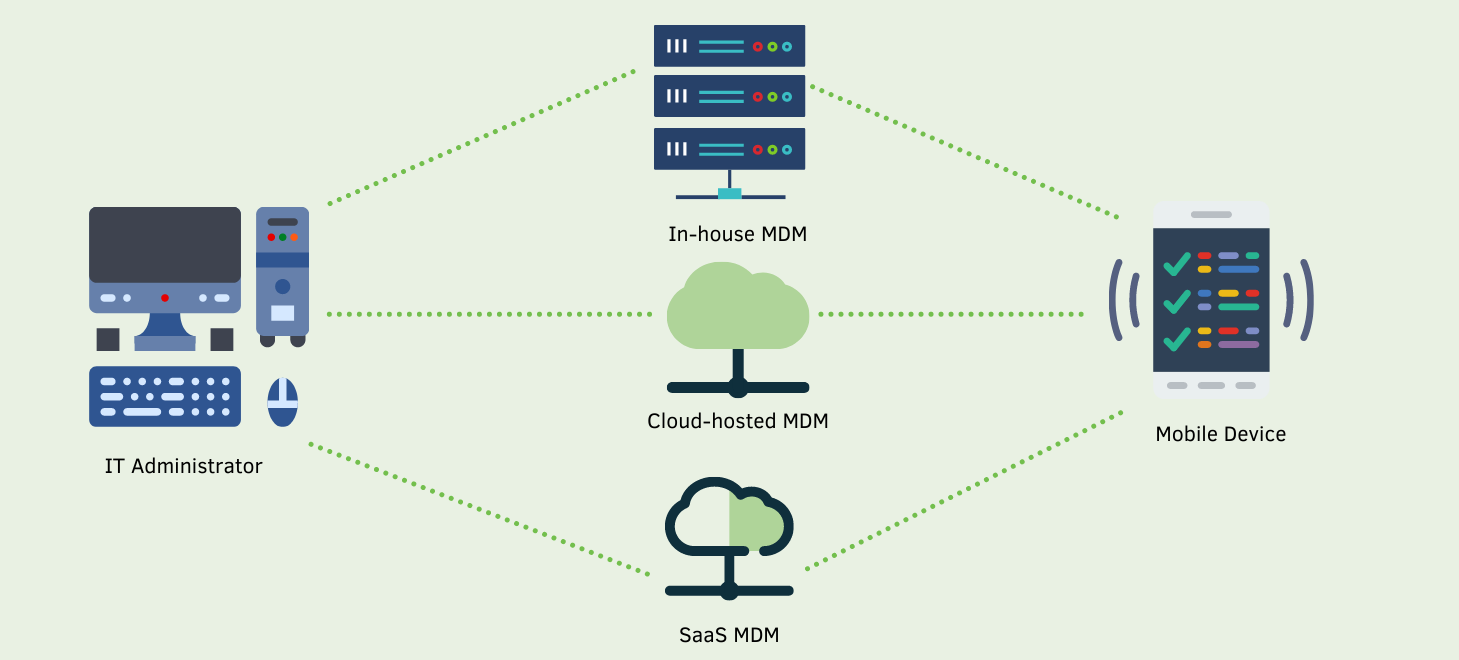
What is Mobile Device Management (MDM)?
Mobile Device Management, or MDM, is a type of security software that allows IT administrators, to secure data by remotely enforcing policies on laptops, smartphones, tablets, and other mobile devices within their organization. Mobile Device Management is the foundation of Enterprise Mobility Management, or EMM, which combines services, solutions, and technologies, such as mobile application management and mobile content management, to secure corporate data on employee devices. This form of endpoint management extends the security of your organization's corporate network to both company and employee-owned devices.
How Does Mobile Device Management Work?
Mobile Device Management (MDM) can be broken down into two components: the MDM agent and the MDM server. The MDM agent lives in the devices that will be managed through this software, and the MDM server lives in your organization's data center.
An IT administrator can configure policies through the server management console and push them out to all MDM agents on devices. These MDM agents apply it to the devices by using the API, or application program interfaces, already built into the devices operating system. Essentially, your IT team remotely creates policies to enforce across all devices that may access company data and remotely implement them on all necessary devices.
In a nutshell, mobile device management can be explained in 5 simple steps
1. Enroll Devices: Register new or existing devices
2. Configure: Setup devices with common configurations
3. Collect: Collet data such as tamper, leak detection, low battery, reverse flow, and more
4. Secure: Enforce security policies to keep devices secured
5. Monitor: Centrally manage and monitor all devices
Blog post: How to build your multi-layered security plan.
Benefits of Mobile Device Management
The benefits of MDM are significant, especially when it comes to information security and productivity. MDM software allows your organization to protect critical company data in ways that would be nearly impossible otherwise. With features such as device inventory and tracking, remote wipe of desktop, password policy enforcement, app blocking, data encryption, and more, your organization can be prepared for any situation. Additionally, this software can help deploy, configure, and update mobile applications to simplify management and save your IT team time.
Uses Cases and Benefits of Mobile Device Management
1) One of your employees accidentally forgets their work laptop, full of sensitive company data, on a bus when coming home from the office. Accidents happen- but if the data lands in the wrong hands your organization could be in big trouble. With Mobile Device Management, the employee would simply need to notify IT staff of the situation, and the laptop can be locked, wiped clean, or encrypted until recovered. This can dramatically reduce the risk of a data breach, and can save your organization thousands from a ransomware attack or fees for being non-compliant.
2) You notice that your team's productivity is down, and think it has to do with a new application everyone's been talking about. Warnings about not playing games during work time hasn’t improved the situation and you'd like to take it one step further. You can work with your IT team to blacklist specific applications, such as this application or games, or whitelist only the productivity applications you know your team needs. This can diminish wasted time and increase productivity and efficiency.
3) Both your organization's management team and employees have shown interest in implementing a Bring Your Own Device, or BYOD, policy, where employees will be responsible for working on their personal devices. Unfortunately, this can create issues with unsafe storage of company data and lack of compliance. With Mobile Device Management, your IT team can configure policies for safe data storage, enforce strong passwords, and more to help increase security and maintain compliance.
Read about managed IT services. What are they and why are they beneficial to your organization.
Mobile Device Management Software Comparison
While there are many types of Mobile Device Management software your organization can purchase, we typically recommend one of the following three options to our clients:
Microsoft InTune

Microsoft Intune is Microsoft's native Mobile Device Management software. This could be the right option for you if your organization already uses Microsoft licensing as well as Azure Active Directory. Intune is integrated with Azure Active Directory to allow your IT administrators to control who has access to what and can also be used with Microsoft 365 applications like Teams, OneDrive, and more. It includes mobile application management, so your IT team can add and assign apps to specific users or group, configure apps to start or update automatically, and track app usage reports. Additionally, InTune can separate your organization's data from the employee's personal data, so if a device needs to be wiped, it can leave employee data intact. This software can be purchased as a standalone Azure service, as part of a Microsoft Security License, or included in Microsoft 365 licensing options.
Learn about Microsoft 365. Here is the ultimate guide to Microsoft Office 365 licensing.
Cisco Meraki Systems Manager

Cisco Meraki Systems Manager can easily integrate with your current network to increase visibility and security. You can pre-enroll devices to be managed, or you can have them added dynamically as more users join your organization. Similar to InTune, you can push applications or restrict content based on specific user groups as needed. You can also track devices anywhere in the world, view on-demand visibility reports on the device's health, security, and software inventory, all while securing the device according to your IT policies. If your organization uses contractors, Meraki Systems Manager might be the right option for you since you can limit how long a specific device has to access corporate assets, allowing the contractor to get the job done without keeping any company information.
Codeproof MDM

Codeproof MDM is an all-inclusive solution that offers standard and unique MDM features, like DriveSaf and Geofenced camera blocking. DriveSaf uses a phone application to block calls, texting, and app using during driving to increase driver safety. Geofenced camera blocking disables the camera function on devices within specified areas to prevent photos or videos from being taken. This option also allows you to increase productivity by blacklisting or whitelisting specific applications, website, and content. It also uses containers to separate user's personal data from corporate data, so a data wipe will leave your employees information intact. Additionally, you can receive alerts in case of security incidences and neutralize them automatically. This solution has a high quantity of features and could be the right choice for your organization if you aren't sure what features you need yet.
|
|
Operating Systems Supported |
Quantity of Device Limits |
Support |
|
Microsoft Intune |
Apple iOS 12.0 and later, Mac OS X 10.13 and later, Android 5.0 and later, Windows 10 |
15 per user |
Ticket system, or purchase premium support |
|
Meraki Systems Manager |
Apple iOS 5 and later, Mac OS 10.7 and later, Chrome OS, tvOS, Android 4.4.4 and later, Windows 10 |
No limit |
24x7 phone support |
|
Codeproof MDM |
Apple iOS 5 and later, Mac OS 10.7 and later, tvOS 9 or later, Andriod OS 2.1 and later, Windows 10 |
No limit |
24x7 email support, phone support Monday-Friday 9 am-6 pm |
Next Steps?
Mobile Device Management can help your organization maintain compliance, increase security, and improve productivity. From features such as device GPS location, whitelisting/blacklisting specific applications or websites, data encryption, etc, MDM can help your IT admin truly manage the devices that carry important corporate data. Contact Datalink Networks today to learn more about Mobile Device Management and what platform is better for your organization.
Click here to see our top 5 benefits of a Managed Service Provider.