
Security Risk Assessments
Receive comprehensive audits and analytics through our security assessments and scans that identify the security and compliance gaps within your organization. Our engineers will assess your security vulnerabilities and deliver a comprehensive security risk assessment.
Our risk assessments consider your company size, industry, compliance requirements, and more. Our team of experts will analyze every aspect of your business and recommend changes that can help your company protect itself against potential cyber threats.

Cybersecurity Consulting
There are many technology options to choose from when building a secure network. Datalink Networks helps you tackle these complex issues by reviewing your current network infrastructure to ensure that your security technology protects your organization against an ever-evolving threat landscape. Our security engineers will then provide you with recommendations and design a cohesive security infrastructure.

Business Continuity and Data Recovery
When architecting your backup systems, Datalink Networks sizes your data, both on-premise and in the cloud, your number of locations, and your requirements for uptime. We will then select the B/DR partners that best fit your requirements.
Our services include migrating your data to the new backup system, annual backup, and restoral testing to ensure that your business is ready to withstand any ransomware attack or natural disaster.
.png)
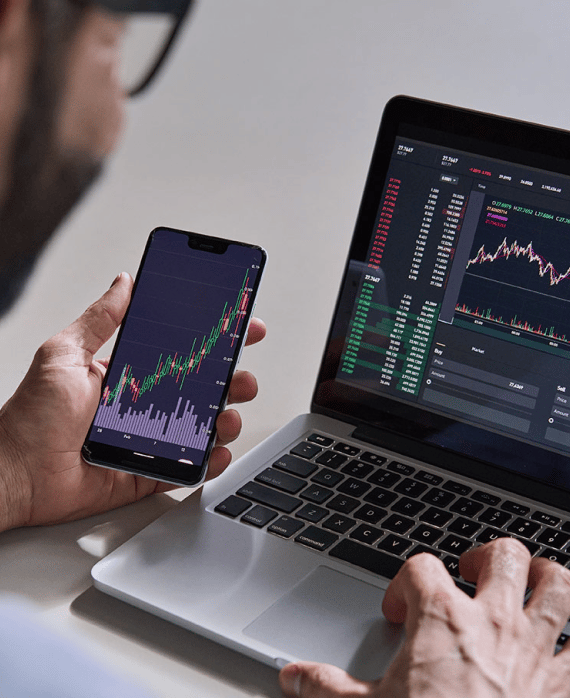
Network Security Monitoring
Prevent attacks before they occur with 24x7x365 network security monitoring services. Receive real-time cybersecurity monitoring that provides visibility into the cyber threats attempting to enter your organization.
Our team complements your internal IT resources by providing in-depth network security monitoring that helps you meet compliance requirements under industry regulations. Our team of experts handle the management of logs and provide actionable recommendations upon sending alerts or reports.


Incident Response Plans
A sufficient response plan offers a course of action for all significant incidents, such as a massive network data breach that can impact your organization for days or even months.
When a significant disruption occurs, your organization needs a thorough, detailed incident response plan to help IT staff stop, contain, and control the incident quickly.
Datalink Networks works with your team to create an incident response plan that will include assigning roles and procedures aligned with your organizational requirements and operations.
.png)
Penetration Testing Services
Our penetration testing services assess the efficacy of your security controls and examine the strength of your overall cybersecurity posture. Our security professionals simulate real-world attacks using the latest adversary techniques to illuminate unknown weaknesses and identify gaps in your security coverage.
We simulate high-impact security breaches to empower you with the knowledge and tools you need to protect your organization against advanced cyber threats proactively. Don’t wait until it’s too late!


Information Security Gap Assessment
To ensure your network is robust and effective, you must conduct an information security gap assessment to identify areas of weakness within your network security controls.
Datalink Networks helps your team conduct this analysis based on your industry-standard security framework including, HIPAA, PCI, NIST CMF, ISO 27001, etc.
Our team of experts then evaluate your staff and IT process to assess your environment and provide a strategic roadmap to accomplish all information security requirements and find the vulnerabilities within your IT security infrastructure.
Why Choose
Datalink Networks?
With over 30 years of experience serving mid-market and enterprise clients nationwide, Datalink Networks has the track record to be your trusted IT-managed service provider.
We go beyond the scope of traditional advisers: We’re engineering entrepreneurs who value creative agility in tackling business priorities. We will take ownership of your challenges as we assess your current infrastructure and help your transition to seamless, scalable, and affordable new technologies that deliver benefits to your users and meet your long-term business goals.
We have successfully designed and implemented solutions for industries that include financial services, insurance, retail, healthcare, utilities, manufacturing, government, and education.
Our Process

Assess Current IT
Environment

Perform Network
Security Assessment
Present & Sign
Proposal
Assign
Account Team

Manage,
Report, Support
Contact us to get started!
Equip your team with the support, knowledge, and tools to provide optimal security for your organization. Improve your security posture by trusting Datalink Networks to monitor, test, and remediate your network. Contact us today to get started!







.png?width=125&height=125&name=5.%20Incident%20Response%20Plans%20(1).png)
.png?width=125&height=125&name=6.%20Penetration%20Testing%20(1).png)
.png?width=125&height=125&name=7.%20Information%20Security%20Gap%20Assessment%20(1).png)