Whether you're back in the office, working from home permanently, or anywhere in between, having a unified communications platform like Microsoft Teams can help improve your team's collaboration and communication efforts. As with any platform or software your organization uses, it's important to configure Teams in a secure way. Let's explore some settings and tips on how to make sure your users and data are protected in Teams.
Table of Contents
1. Overview of Microsoft Teams
2. Microsoft Teams Security Features
3. Microsoft Teams Best Practices
Is your Network Secure and Compliant? Learn more about our complimentary security audits. Our audits not only identify security risks, but also identify unused / underused seats.
We typically identify over 20% in license savings! Speak to a Microsoft Expert today!
Overview of Microsoft Teams
Microsoft Teams is a cloud-based communication and collaboration platform with 145 million daily users as of April 2021. This platform can run off of a desktop, web, or mobile application so your team can be productive anywhere and from any device. Teams is typically the best unified communications solution for organizations that already have Microsoft licensing, as it is included in most business licenses and ties in with the applications your team is already using like OneDrive and SharePoint.
Teams includes several useful features like:
Chat
Instant message with individual users or groups of users to aid in collaboration and quick communication. In chat, you can quickly send and receive files, see the presence of other users, and call them all from the same screen. The chat function can often replace Slack, Skype for Business, or other instant messaging platforms your organization may already be utilizing.
Teams and Channels
Teams help segment your entire organization into subsets for various job functions or groups that commonly work together. Channels help further organize Teams based off tasks, topics, or other criteria you find useful. Teams and channels can be built as public, so anyone in your organization can join, or private, where users need an invitation.
For example, you can create a Human Resources Team that includes all users within your organization. One channel can be for announcements, where your HR representative details required training, surveys, or other HR needs. Then, a private channel can added with just the HR staff as members. In this channel they can plan, coordinate, and collaborate on their tasks. Teams are easily customizable to fit the needs of your organization.
File Sharing
Within Teams channels, you can use any of the standard Microsoft Office applications, like Word, PowerPoint, and Excel. These documents belong to the channel as a whole, so all users within the channel have access to view and edit this documents in real-time. This can help your teams collaborate more seamlessly and help management keep up to date on progress of projects.
Calendar
Your Teams calendar and Outlook calendar tie together, so they are both fully up to date. With Teams calendar feature, you can book Teams and in-person meetings, complete with a Teams link or alternate designated location. Additionally, you can use the Scheduling Assistant to see when your colleagues are available for meetings to help limit double-booking situations.
Video Calls
Video Calls through Teams can replace Zoom, Go2Meeting, Webex, or other paid video conferencing platforms. Through Teams you can both schedule video calls or use the "meet now" function to immediately schedule a call with someone. Additionally, when you're in a call you can screen share, record, message, take notes, and more.
Microsoft Teams Security Features
Like every other platform your organization uses that stores important company data, it is crucial that you secure Microsoft Teams. When preparing to deploy Microsoft Teams, the settings you configure can help improve its overall security. The following 5 configurations can be used as a guide to create a more secure environment for your users.
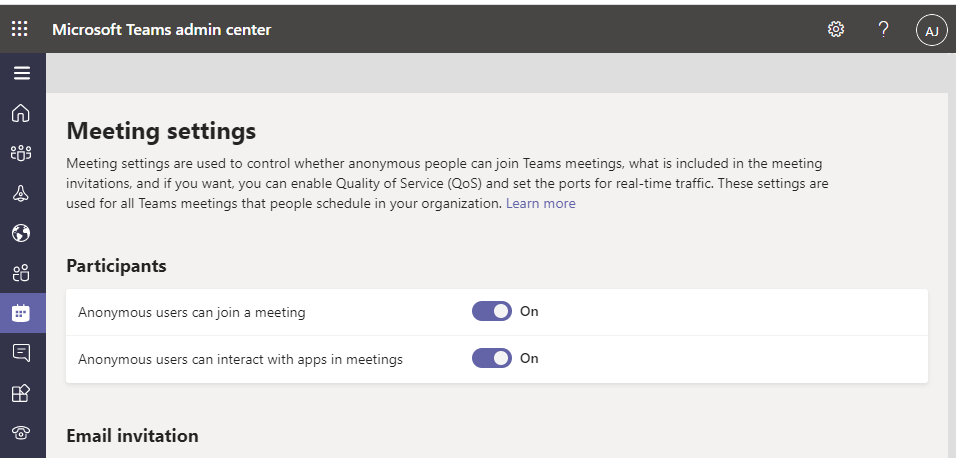
1. Invite-Only Microsoft Teams Meeting
The term "Zoom-Bombing" came into existence over the latter half of 202o. The term is used to describe the scenario when someone joins and disrupts your meeting with inappropriate audio, video, or screen sharing content
Configuring invite-only meetings can help prevent this situation from happening. With this setting, users have to be explicitly invited to a meeting to be automatically admitted. If someone tried to join the meeting without their email address listed as an invited participant they would be placed in the lobby for someone to admit them.
Additionally, you could also set Teams to place all outside users in the lobby and require an internal user to grant them access. This can help prevent malicious users from being disruptive or accessing the private data discussed within the meeting.
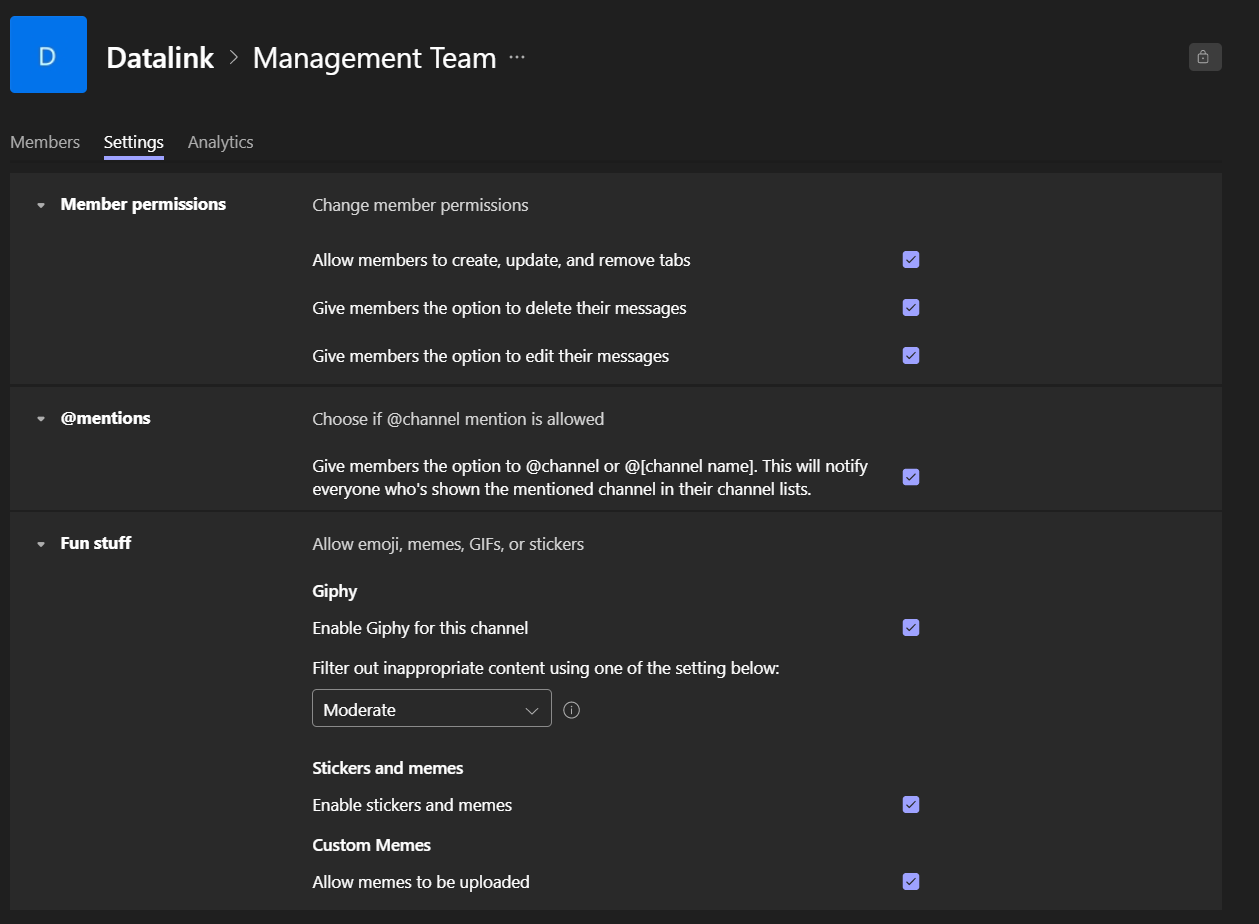
2. Enable Channel Moderation
With Channel Moderation, the channel owner and any other designated users can act as moderators for the group. These users can be in charge of specific tasks within that teams channel, such as starting new posts, deciding whether or not to allow other members reply to channel messages, and more.
This can keep your users on task as well as delegate overseeing Team activity to specific users to ensure that nothing is out of order. By default, channel moderation is off, but it can be turned on by IT admin at any time.
3. Manage Applications in Microsoft Teams
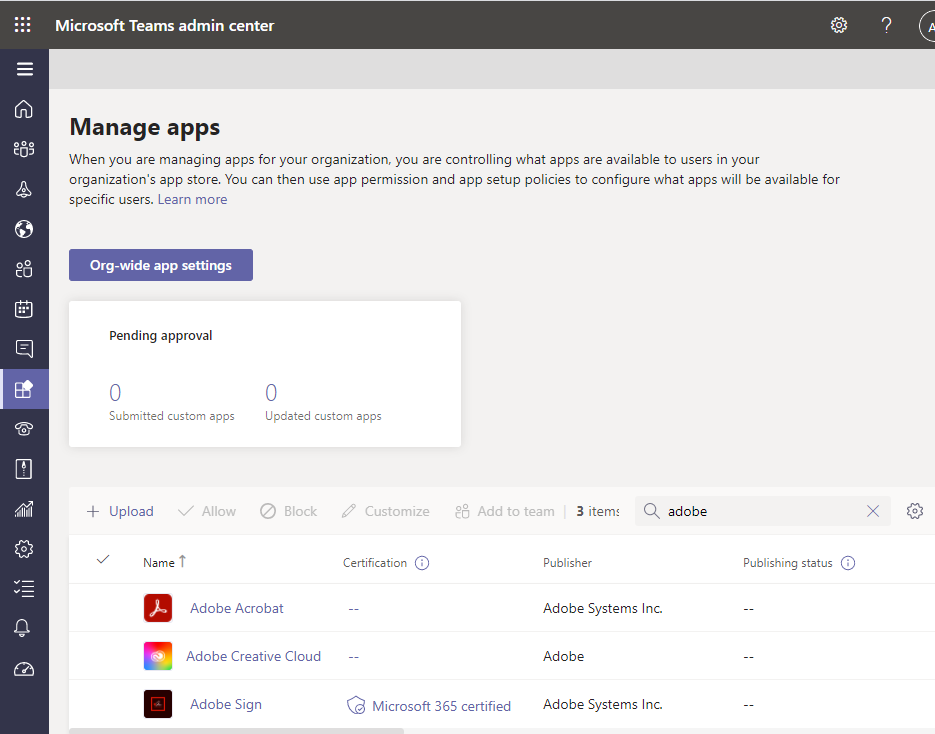
Microsoft Teams has hundreds of third party applications and integrations to create an all-in-one collaboration platform. Keep your staff on task and limit areas for potential attack by managing all third party applications.
Block unnecessary or unverified applications across the entire organization, or use custom app policies to block or allow applications for specified users. Applications certified by Microsoft will have a badge associated to the app. See image above for an example
4. External and Guest Access Policies
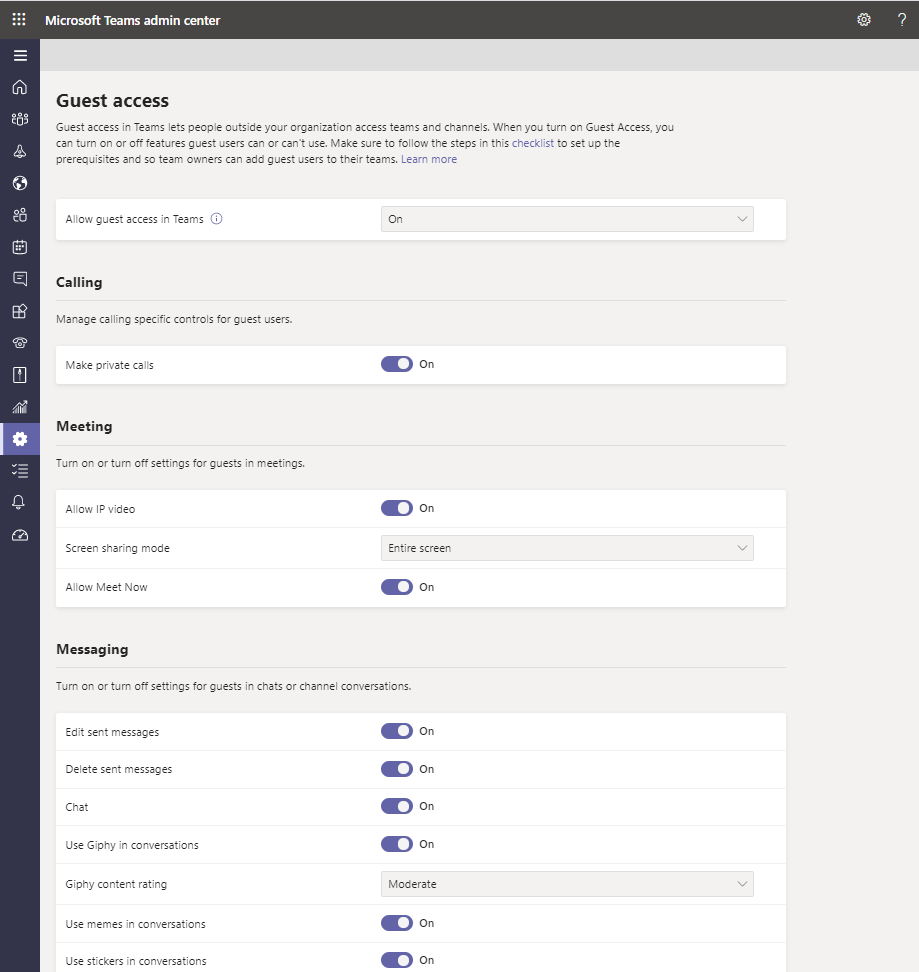
Teams allows your organization's users to communicate and collaborate among themselves and with users not in your tenant. This feature can be incredibly helpful when working on projects with clients, communicating with vendors, and sharing content with partners. If there is a concern about private data being shared with external users you can turn this function off in admin center.
External Access allows your users to find, call, chat, and meet with users outside your organization but does not allow them to be placed in Teams or Channels with them. Some organizations may find this to be a security risk or distraction for their users. If you want your users to not be searchable to external users, this feature should be turned off.
Guest access is similar to external access, although it allows your users to be placed in Teams and Channels with users not in your tenant. Like with external access, this can be turned off or specifically designed to meet your needs. You can turn off private calls, meet now, screen share, and chat if desired to keep all communications public within the channel. This can prevent a malicious user from privately sending data through Teams and increase visibility on communications with guest users as a whole.
5. Utilize Policy Templates
Policy templates are pre-defined policy settings that are used to address common security and compliance issues. These were initially created for schools, but are available and useful for all types of organizations. These templates monitor communication to protect against offensive language, harassment, and sensitive company information. Monitoring communication can also help avoid conflict of interest between individual or groups of users. It also helps maintain compliancy and security by monitoring information related to regulatory finance compliance.
While these configuration will make your Microsoft Teams tenant more secure, it does limit your users functionality. By implementing all or some to best fit your organization, you are increasing your security right within the Microsoft Teams Admin Center.
Microsoft Teams Security Best Practices
Besides the setting configurations outlined above, there more security best practices your organization can follow to increase your Microsoft Teams security.
1. Backup your Microsoft Teams Data
Many users believe that Microsoft backs up their tenant since it is stored in the Cloud, but unfortunately this is not the case. Microsoft is not responsible for any loss of data, including reasons such as: malware, malicious users, natural disasters, Microsoft outages, and more.
In the event that you have a malicious user who deletes important company data stored within Teams, having a backup can ensure that nothing is permanently lost. Manufacturers like Barracuda, Datto, Arcserve, and Veeam all offer a full Microsoft backup solution with quick and easy recovery.
Learn more about Office 365 Data Backup by visiting our blog today: Best Office 365 Data Backup Solutions
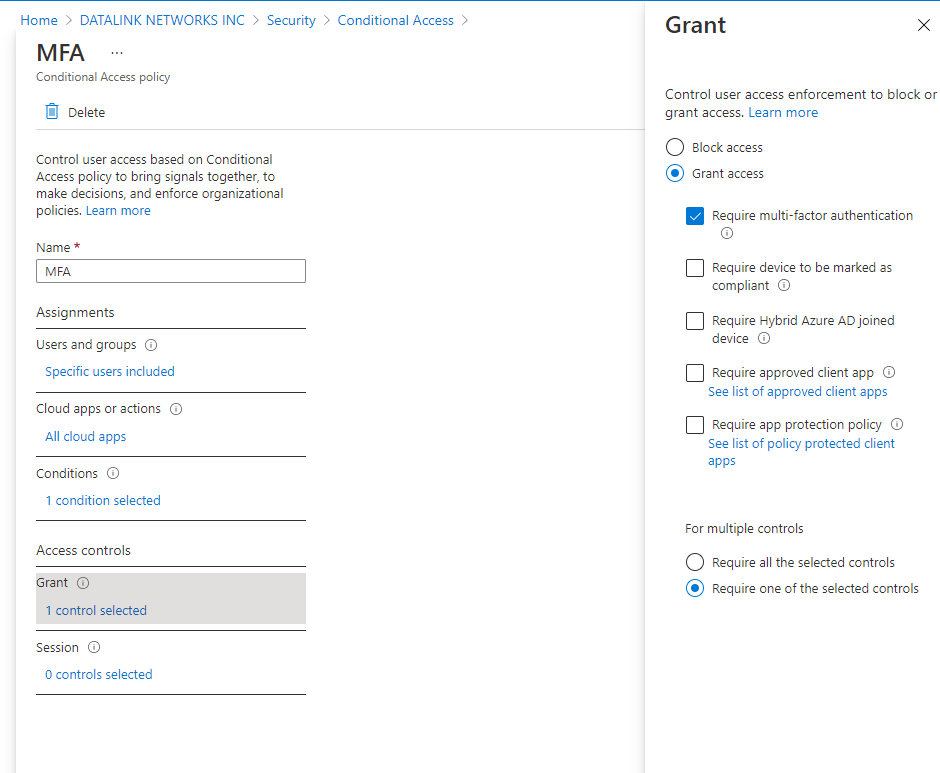
2. Enable Multifactor Authentication for Microsoft Teams
Enabling multifactor authentication or conditional access policies can also help provide extra security for your Microsoft tenant. Multifactor authentication is a standard security practice that requires users to use a second method of authentication beyond just their password, such as a code sent via text, through an app, or by phone call.
Conditional access policies are if/then statements that determine whether a user should be required to authenticate or not. Common conditional access policy signals are IP location information and the device requesting access. For example, if you don't want your users to have to use multifactor authentication when they are in their designated working locations, such as office or at home, conditional access policies will recognize these locations and grant access. If, however, they are in a hotel on a business trip, the unusual location will require authentication.
3. Enforce Least Privileges for Microsoft Teams
Another common security tip is to enforce least privileges across your Microsoft tenant. This helps protect your tenant in the event that a user has been compromised as the surface area of potential attack is lowered. For instance, if a lower level user is hacked but has significant administrative roles, this attack can go much further into tenant. If this same user had no administrative roles, because their job function didn’t require it, the compromise would stay in just the areas they have access to and no major changes would take place within the tenant.
Next Steps?
To properly address the security within your Microsoft tenant, you can schedule a complimentary Microsoft 365 Health Check Assessment with our team today. Not only will this assessment uncover unused and unassigned licenses but it will provide recommendation on how to tighten your Microsoft security. Find and fix your vulnerabilities by discovering who is spreading malware, sharing files dangerously, or have insecure passwords. Contact us today to get started!